Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
The following are the key terms and concepts used within Zentitle2.
Grace Period
A grace period in software licensing is a specified amount of time given by a software vendor after a subscription (time-based) license has expired, during which the software can still be used without penalty or disruption.
This period is designed to give users time to renew or update their licenses without having to stop using the software immediately. The grace period can vary depending on the software vendor and the specific license agreement but typically ranges from a few days to a few weeks.
It's important to note that the grace period does not extend the license term, and users must still renew or update their licenses within the designated time frame to avoid any potential legal or financial consequences. Also note that the renewal period starts when the prior term expired rather than extending from the end of the grace period.
Lease period
The lease period in software licensing specifies the amount of time the application can run locally with a cached view of the license rights before forcing a refresh of those rights from the cloud-based repository (or a local license server).
Note: the lease period is completely independent of the term of the license itself (the license could be perpetual, a subscription, etc.).
Plan
Plans also define the activation rule that should be used for entitlements with that plan - such as 'Activate upon first use,' 'Activate upon creation,' and 'Activate Manually'. Sample plans may include a 1-year subscription, a perpetual (non-expiring) license, a 30-day trial, etc.
You can define as many plans as you wish, subject to your subscription.
License type:
Perpetual
A perpetual license is a type of software license that grants the user the right to use the software indefinitely, without any time limitations. With a perpetual license, the user typically pays a one-time fee upfront for the right to use the software for as long as they want, without any ongoing fees or subscriptions.
Under a perpetual license, the user is often entitled to technical support and software updates for a limited period, typically one year. After that, they may need to purchase a new license or renew their support agreement to continue receiving updates and support. However, the user can continue to use the software without interruption even if they choose not to renew their support agreement. The license itself will often include the ‘maintenance expiration date’ so that it can be appropriately enforced or communicated.
Perpetual licenses are common for many types of software, including desktop applications, server software, and some enterprise software. They are often contrasted with subscription licenses, which require the user to pay a recurring fee to continue using the software.
License type:
Subscription
A subscription license is a type of software license that grants the user the right to use the software for a limited period, usually for a fee that is paid on a recurring basis, such as monthly or annually. With a subscription license, the user does not own the software but instead pays for access to it for the duration of the subscription.
Under a subscription license, the user typically receives all software updates and technical support for the subscription duration. However, once the subscription period ends, the user must renew to continue using the software. If they choose not to renew, the software will no longer be accessible to them.
Subscription licenses are common for many types of software, including cloud-based applications, software-as-a-service (SaaS) products, and some enterprise software. They are often contrasted with perpetual licenses, which allow the user to own and use the software indefinitely after a one-time payment without any ongoing fees or subscriptions.
Note that software trials are a form of subscription license - with the end-user typically gaining access to the software for a short fixed amount of time (typically 30 days) for no charge.
License Start
Entitlements can be activated
on creation = Plans: License Start set to Entitlement Creation
or first use = Plans: License Start set to Activation
or manually = Plans: License Start set to Manual Activation - by using “Activate Now” button on Entitlement details page
This is the case for both Subscription and Perpetual License Type.
Offering
Often used interchangeably with “SKU” (Stock Keeping Unit) or “Part Number” - see below for SKU.
Together, the combination of an edition and a plan defines an offering.
Offerings often equate to a "price book" or SKU list in your systems, such as your CRM, ERP, or billing system. Per your Zentitle subscription, you can define as many offerings as you wish.
Entitlement
Entitlements track what your customers have purchased and all changes through the lifecycle.
In software licensing, entitlement refers to a customer's specific rights and permissions to use a particular software product. An entitlement is essentially a record of what a customer has purchased, determining what they can do with the software.
Entitlements can include a wide range of permissions and restrictions, depending on the specific licensing agreement. Some common examples of entitlements include:
The number of users or devices that are allowed to access the software
The specific features or modules that are included in the license
The geographic location or territory where the software can be used
The duration of the license, including start and end dates
The level of technical support that is included with the license
Any restrictions on how the software can be used or distributed
Entitlement management is an important part of software licensing, as it helps ensure that customers are using the software in compliance with the licensing agreement. By tracking entitlements, software vendors can ensure that customers are only using the software within the limits of their license, which helps prevent misuse and piracy.
Product
The “Product” in the Zentitle2 context typically refers to a given application or binary. Depending on the business model, most products are then broken down into price plans and editions.
License definitions are typically specific to a given product (i.e. a Word license may have features defined for access to dictionaries, thesaurus, etc., whereas an Excel license might have features related to pivot tables, etc.)
Edition
An “Edition” is a variation of a given product - with the classic example being a “Good,” “Better”, or “Best” progression of increasing functionality at different price points..
An edition is a subset of a Product in the third tab under the product menu.
Feature
A “Feature” in the Zentitle2 context is a boolean flag that determines whether a given feature / module / component should be enabled for a given user.
Attribute
An “Attribute” in Zentitle2 is a key/value pair that can be used to store useful information in the license, such as the customer name, etc.
It can also be used to represent aspects of the business model for the license itself, such as the number of licensed devices, lists of integrations that should be enabled, etc.
In Zentitle2, the attributes are typed and can be Integers, Strings, or Dates. They are equivalent to “Application Agility Fields” in V10.
Advance Feature: Usage counter
An entitlement can have one or more ‘usage’ features. Consumption tokens can be used to track measures of usage over time. For example, you may have a 1-year subscription that provides 1000 report runs over the year.
The usage feature would track how many reports had been run so far (with the application deducting one from the count each time the report is run).
Advance Feature: Element Pool
Element Pools represent a concurrent aggregate count of some measure. For example, let’s say there is a storage management cluster and the business model was to charge for the aggregate amount of storage under management across the cluster.
Each node would check out from the element pool the quantity of storage that node was managing (50TB, 100TB, etc.) and the licensing would enforce that at no time was the aggregate amount of storage licensed ever exceeded.
Activation Codes
In Zentitle2, a given entitlement may have multiple valid activation codes - any of which can be used to activate a seat against the entitlement.
SKU
SKU stands for "Stock Keeping Unit," which is a unique identifier used to track individual products in inventory management and sales. In the context of software licensing, a SKU is a code or number that identifies a specific software product or licensing option.
SKUs are used by software vendors to keep track of their inventory and sales, and to ensure that customers receive the correct product or licensing option when they make a purchase. For example, a software vendor might use a SKU to differentiate between different versions of their software, such as a basic version and a professional version, or to track the number of licenses that have been sold for a particular product.
SKUs can also be used by resellers and distributors to track their inventory and sales, and to ensure that they are ordering and selling the correct products. When a reseller or distributor orders a product from a software vendor, they will typically provide the SKU number to ensure that they are receiving the correct product. Similarly, when a customer purchases a product from a reseller or distributor, they will often receive a receipt or invoice that includes the SKU number to confirm what product they have purchased.
Concurrency mode: Concurrent
Concurrent (also called ‘Floating’) licenses allow a maximum number of concurrent seats active on the entitlement at any one point in time. Upon startup, the application would attempt to check a seat out of the license pool, and check it back in one the application terminates. If the application dies without explicitly returning the license then the seat will automatically be returned once the current lease period expires.
Concurrency mode: Node Lock
Node lock licenses are meant to be permanently activated against a given machine / seat and are not returned upon terminating the application. They are persistent licenses (not to be confused with perpetual licenses).
Seats
Seat count - number of seats available on Entitlement that has been set from Offering that this entitlement has been created with, but can be amended on Entitlement level.
Seats used - currently used seats
Seats - overview on seats used from seat count, presented in form of 3/21
Webhooks
Webhooks are a type of callback mechanism used by web applications to provide real-time notifications to other systems. Essentially, a webhook is a way for an application to send data to another application automatically when certain events occur.
The basic idea behind webhooks is that one application sends an HTTP POST request to a URL specified by another application, indicating that a certain event has occurred. The receiving application then processes the data in the request and takes appropriate action based on the content.
Webhooks are commonly used in a wide variety of applications, such as:
Integrating with third-party services to receive notifications when specific events occur
Triggering custom workflows or automation tasks in response to user actions
Updating data in real-time across multiple systems and applications
Automating data synchronization between different systems
Webhooks can be thought of as the opposite of an API, which requires the client application to poll the server for updates. With webhooks, the server actively pushes data to the client, eliminating the need for the client to poll for updates and reducing server load.
Activation Usage History
A graph that shows the usage (typically active seat count) of a license over time
Seat Count is the allowed number of seats that can be used with this Entitlement.
Min and Max is maximum and minimum count of used seats at any given moment during the day. For example:
activate: max 1, min 1, current 1
deactivate: max 1, min 0, current 0
activate: max 1, min 0, current 1
activate: max 2, min 0, current 2
deactivate: max 2, min 0, current 1
deactivate: max 2, min 0, current 0
End User Portal
The end user portal (EUP) is an option to help your end users manage their entitlements and do "offline" activations/de-activations.
A pre-built way for users to manage their entitlements saves support time and costs.
The end user portal can be customized to fit in with your branding.
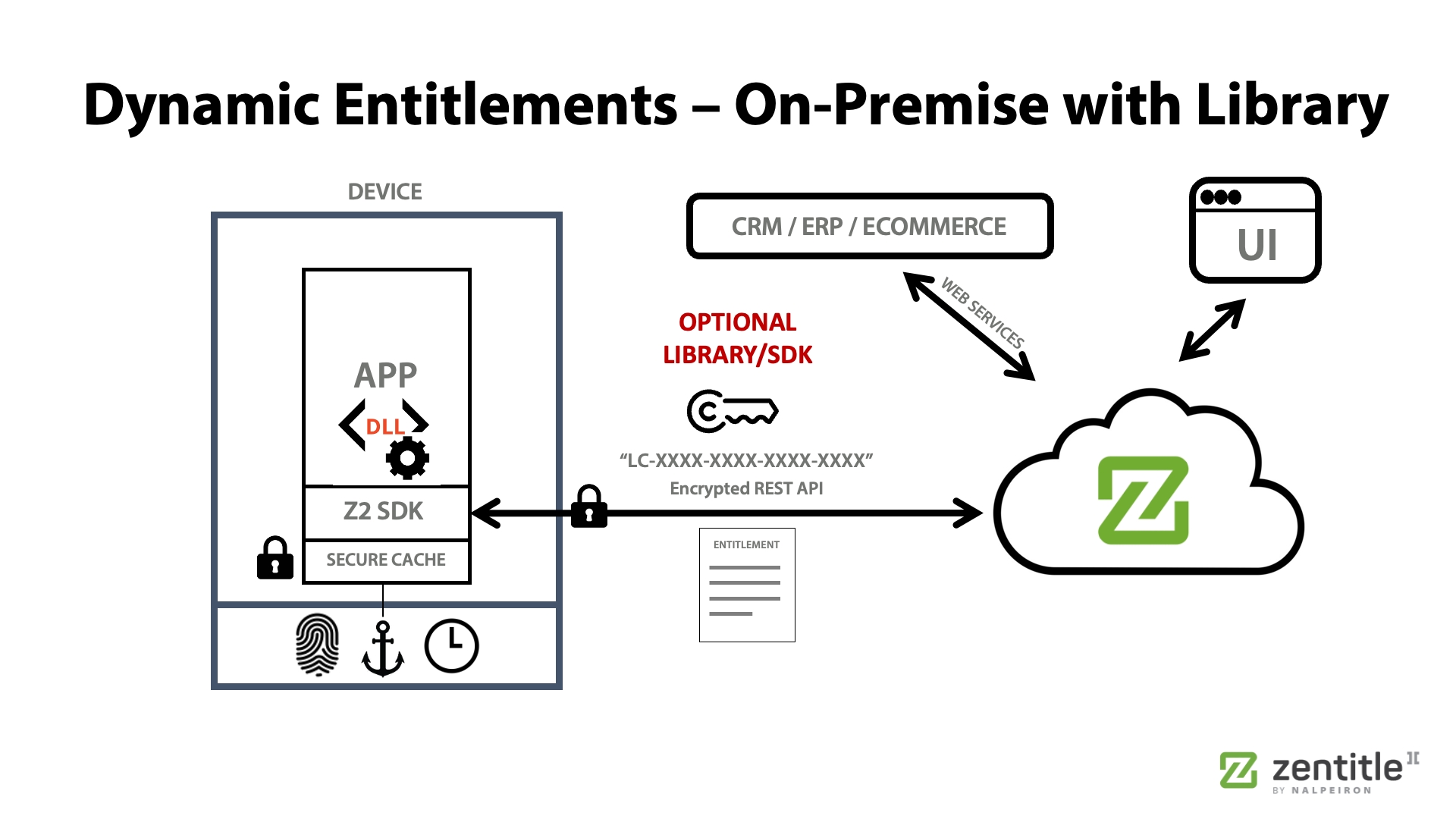
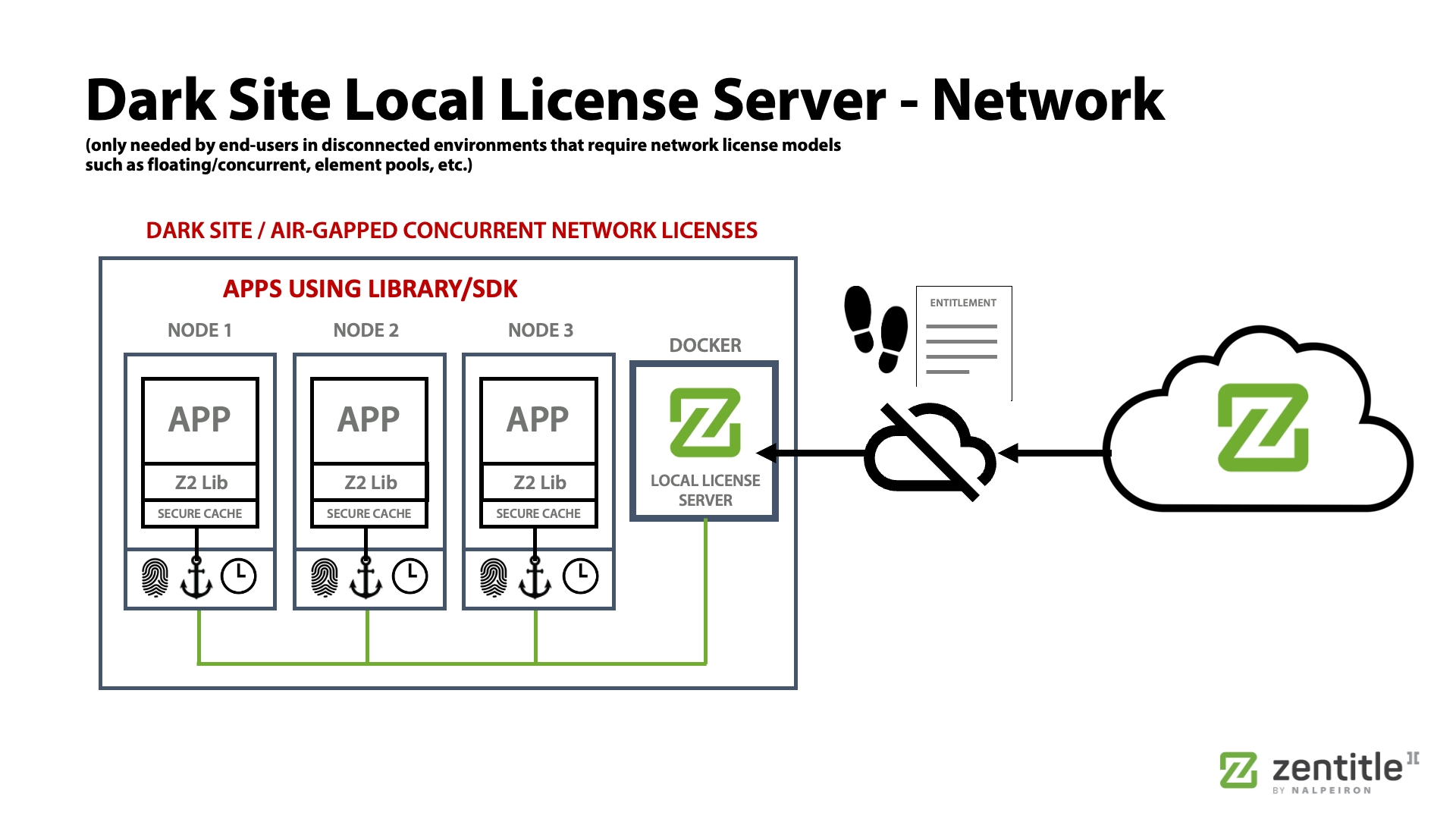
Local License Server (LLS)
The Zentitle2 Local License Server allows the vendor to deploy a docker-container-based server to an end customer who does not want to (or cannot) allow an ongoing connection with the Zentitle2 cloud-based license server. Often also called "Dark Site" Local License Server (that enables Network-based licensing).
LLS provides similar functionality to Zentitle2 in the cloud.
Once you have your Local License Server (LLS) running, you can delegate a given entitlement to that LLS by going to that entitlement and changing the 'Entitlement Host' to the appropriate LLS instance.
Account Based Licensing - ABL (Identity-based licensing)
Account Based Licensing is the process of managing users’ accounts and giving users access to software or an application, typically via a username and a password or an external identity management solution such as Microsoft Azure AD, Okta, OneLogin, Ping Identity, ForgeRock, Auth0, and Oracle Identity Manager.
Zentitle2 enables both types of application access and also allows you to choose the best-of-breed identity provider you or your customers are using.
Accounts replicated from the vendor's authentication platform are called "OpenID Token authentication."
Accounts created and managed within Zentitle2 are called username/password authentication.
Virtual Machine Control - nonce
Today, most desktops are virtualized, and the same has been true for servers for years. This means that Licensing has to deal with issues related to impermanent storage and copying of deployed application instances.
Abuse of VMs leads to lost revenues and improper use of the customer's IP.
To help with managing VMs, Zentitle has created the concept of the Licensing API: Nonce.
The API uses a nonce concept. Every request must contain a unique nonce value in the N-Nonce header. First, the Create Activation endpoint returns the Nonce. The application needs to store this nonce and use it in subsequent requests. Subsequent requests will return a new nonce, which needs to be used in the next request. Nonce values are returned in the N-Nonce header.
allows you to activate an entitlement using the end user's login credentials (Username/password) instead of the more "on-premise" based license key/code/activation code.
Let's jump on a call and discuss how we can help, get in touch with your account manager today →
Software activation is a license validation process that verifies a user's right to use a software product. It typically requires a unique activation code or digital identity verification. Its primary purpose is to prevent unauthorized copying, use, or distribution of software, thereby enforcing software license agreements and protecting developers' intellectual property.
How Software Activation Works
Traditional Methods: Software activation traditionally relied on product keys—strings of letters and numbers provided with boxed software or via email. Users would enter this code during installation or first launch. The software would verify the code against a database to confirm its validity. Activation codes were often tied to specific devices or hardware configurations to prevent sharing.
Validation Process: The software sends data (like the product key and device ID) to the vendor's server during activation. This verifies that the license is valid and not already in use. Upon successful verification, the software becomes fully operational. If verification fails, users must enter a valid code or accept limited functionality.
Modern Approaches: Cloud computing and SaaS have shifted activation methods to focus on digital identity, typically through verified email addresses rather than device-specific codes. This enables flexible licensing options: node-locked licenses for specific devices, floating licenses for concurrent usage, and seamless account-based access across multiple devices. These systems also offer self-service activation management, improving user experience and reducing support needs.
Benefits and Drawbacks
Benefits:
Prevents unauthorized use and piracy
Ensures only paying customers can access full features
Enables flexible licensing models and feature control
Facilitates compliance with licensing agreements
Allows vendors to monitor usage and manage entitlements
Drawbacks:
Traditional activation methods can be inconvenient, causing friction for legitimate users (e.g., lost keys, hardware changes breaking activation)
Outdated systems may fail to prevent piracy and complicate support
Examples
Traditional Software Example: Boxed and desktop software require a multi-step installation and manual key entry, with the risk of losing the disk or activation code, and no way for the vendor to verify activation remotely.
SaaS Software Example: Modern SaaS Software uses identity-based activation tied to a user's email. Users can access their account from multiple devices, with node-locking and floating license principles ensuring compliance and a seamless user experience. Activation and deactivation are managed through an online dashboard, and the system prevents concurrent unauthorized use by requiring periodic online verification.
Activation vs. Registration
While related, activation is distinct from registration. Registration typically involves collecting user information for marketing or support, whereas activation is a technical process that validates license compliance and enables software functionality.
Software activation is essential for license enforcement and IP protection.
For SaaS identity-based or account-based activation methods offer a better user experience and more robust protection than traditional product key systems.
Effective activation systems balance security, compliance, and user convenience, supporting vendors and legitimate customers.
In summary, software activation is a critical process that ensures only authorized users can access and use software. It has evolved from cumbersome product key entry to seamless, cloud-based, identity-driven solutions.
Zentitle's Cloud-Based Licensing makes it easy for end-users to activate your software. Once the Application is activated, the Entitlements (what features an end-user can and can't use, under what circumstances, and for how long) are delivered from the Zentitle Cloud to your application, which can then be queried by your application to decide how it should behave. Offline Activation is also supported. Zentitle provides you with a portal for this that you can brand. Offline Activation is used when your end-users either have devices that aren't connected to the internet or your application on their device isn't permitted to talk to the internet—both scenarios where their application can't directly communicate with the Zentitle Cloud. Zentitle also offers a LAN Daemon (Local License Server) for licensing within Dark-Site Networks, for business, industrial, and secure locations.
When the end-user's application is activated, the Zentitle Cloud tells it how long its License Check Interval is. The License Check Interval (sometimes known as a Lease Period) is the time after which the end-user's application needs to check with the Zentitle Cloud to determine whether its entitlements are continuing 'as is' or have changed. This check, which happens at the end of the License Check Interval, is called a License Refresh. NOTE: The License Check Interval should not be confused with the Subscription Period (which is something specific only to Subscription-Based Licenses).
The License Check Interval (with the resulting License Refresh) is the driving force behind Dynamic Entitlements. This means that a customer's entitlements are not set in stone forever, in fact you have the ability to change them at any time and these changes are delivered automatically upon any License Refresh, without the customer needing to do anything at all. So, you can kill, add to, or change what parts of your software a customer can use. Automatic processes such as a Subscription License ending when a customer hasn't paid are taken care of. Dynamic Entitlements makes the automatic fulfilment to the customer of upgrades, downgrades, and up-selling and cross-selling possible. When the lifecycle of an end-user's application is under your control in this way, including via e-commerce, CRM, customer support, and via your own backend systems connected to Zentitle using its API, running your business as a Software Vendor becomes much easier.
The License Status, which is accessed through the Zentitle SDK, represents the current status of the License. The License Status is key information you can use within your Application to implement whatever licensing policy you wish. It is also one of the attributes you can query of the License locally. Our example applications will help you get started with this concept. A quick tip to remember here is that a License Status has a numerical value: Any positive value means the client has been given permission to remain licensed by the Zentitle Cloud, but negative values mean the permission to remain licensed has been denied (each value has a meaning; examples for negative values may include Subscription Expired, Too Many Seats In Use, or License Has Been Deactivated). It is important to implement a timer-based routine in your application to periodically check the License Status and have your application behave appropriately to any changes.
Yes, SaaS users can be activated offline, though the process is more complex than standard online activation and typically requires special licensing mechanisms. Offline activation is designed for situations where users or organizations operate in environments with limited or no internet connectivity, such as secure facilities, remote locations, or air-gapped systems.
How Offline Activation Works in SaaS:
Token or File-Based Exchange: Offline activation works by exchanging encrypted and digitally signed files (tokens) between the user's device and the vendor's licensing system. This is necessary because the SaaS platform cannot connect directly to a licensing server. The process involves three steps: generating an activation request file on the offline device, transferring it to an online system (via USB, email, or another secure method), and receiving a response file to complete activation.
Cryptographic Security: All activation tokens and files are encrypted and digitally signed to ensure data integrity and prevent tampering. This security measure ensures that only valid, authorized licenses can be activated, even without an internet connection.
Lease Periods and Expiry: Offline activations typically have time limits. The vendor sets an "offline lease period," and users must renew their access by repeating the activation process when this period ends. The lease expires at either the end of the lease period or the subscription end date, whichever comes first.
Activation and Deactivation: Users can manage their licenses offline by generating a deactivation token and uploading it to the vendor's portal to release the seat. This allows vendors to maintain license compliance and track usage even when systems are offline.
Common Offline Activation Methods:
Limitations of Offline Activation in SaaS:
No Real-Time Feature Management: Advanced features like real-time feature checkout or return are not available offline, as there's no live connection to the licensing API. Some vendors provide local replacements for these APIs, but functionality is generally more limited compared to online activation.
Manual Processes: Offline activation requires manual steps, such as transferring files between systems, which can introduce friction and administrative overhead.
Periodic Renewal Needed: Offline licenses must be periodically refreshed to remain valid, ensuring compliance with subscription terms and preventing perpetual unauthorized use.
Summary
While SaaS is inherently designed for online access and activation, offline user activation is possible through secure, token-based processes that allow organizations to use SaaS products in restricted or disconnected environments. This approach balances the need for license compliance and security with the realities of operating without internet connectivity.
Email-based
User sends an activation request code by email and receives a response to activate.
File transfer (USB, etc.)
User exports/imports activation files between offline and online systems.
Offline activation portals
Vendors provide web portals for uploading and downloading activation files.
A product key or license code is a unique alphanumeric string used to verify that a user has legally obtained the right to access and use a software product. Traditionally, these keys are entered during installation to unlock or activate software, serving as proof of purchase and ownership. In the context of SaaS (Software as a Service), the role and implementation of product keys or license codes have evolved:
Traditional Role:
Product keys are typically provided to users when they purchase software, either as a physical card, in packaging, or via email for digital products.
The user enters the product key during installation; the software then verifies it against a database to ensure it is valid and not already in use.
This process unlocks the full functionality of the software and prevents unauthorized copying or use.
How Product Keys or License Codes Work in SaaS:
SaaS platforms are primarily cloud-based and are accessed via user accounts rather than local installations, so product keys are less commonly used as the main activation mechanism.
When used, a license code may still be issued to validate the initial purchase or to link a subscription to a specific organization or user account.
Instead of entering a product key during installation, SaaS users typically activate their access by verifying their identity (e.g., email confirmation) and associating their account with a purchased subscription or entitlement.
The SaaS provider manages entitlements and access rights centrally, often rendering the traditional product key process invisible to the end user.
Key Differences in SaaS:
Access is identity-based: Activation and licensing are usually tied to a user's digital identity (such as an email address) rather than a device or installation.
Centralized management: The SaaS vendor controls access rights and license compliance through their cloud platform, eliminating the need for users to manually enter product keys for each device.
Ongoing validation: SaaS platforms can dynamically update, revoke, or extend access based on subscription status without requiring new product keys.
Summary Table: Product Keys in Traditional Software vs. SaaS
Activation Method
Product key entered by user
Account-based, rarely uses product key
Access Control
Device or installation-based
User identity and cloud-based
License Management
Local, static
Centralized, dynamic
User Experience
Manual entry required
Seamless, often invisible
In summary:
While product keys or license codes remain a foundational concept for software licensing and activation, in SaaS environments they are often replaced or supplemented by identity-based access and centralized license management. This shift enables a smoother user experience and more robust protection against unauthorized use.
Digital Rights Management (DRM) is a set of technologies and strategies designed to protect digital intellectual property from unauthorized access, copying, and distribution. While DRM is often discussed in the context of media like music and video, it plays a critical—yet sometimes misunderstood—role in the world of software. For software developers and publishers, DRM is not just about preventing piracy; it is an essential tool for enforcing licensing agreements, safeguarding revenue, and maintaining the integrity of software products.
Software piracy remains a significant global problem, costing the industry tens of billions of dollars annually and leading to job losses and lost innovation. Unlicensed software use is widespread, with studies showing that a large percentage of users may run pirated copies—sometimes unknowingly. Beyond revenue loss, pirated software is a major vector for malware and cybercrime, as hackers often distribute compromised versions to unsuspecting users.
DRM for software directly addresses these issues by:
Preventing unauthorized copying and distribution
Ensuring only paying, legitimate users can access and use the software
Helping software vendors comply with complex licensing agreements
Protecting users from security risks associated with pirated copies
Software DRM typically combines several technical and policy-based mechanisms:
Software binaries and critical resources are encrypted. Access is only granted when a valid license key or token is presented. This ensures that even if the software is copied, it cannot be run without proper authorization.
DRM systems authenticate users or devices before granting access, often tying licenses to user accounts, device IDs, or hardware fingerprints. Permissions management allows vendors to specify who can use the software, on how many devices, and under what conditions (e.g., time limits, feature access).
DRM enforces the terms of the software license agreement—such as the number of installations, concurrent users, or duration of access—by monitoring usage and blocking violations. Modern DRM solutions can support a variety of licensing models, including perpetual, subscription, and consumption-based licenses.
Some DRM systems provide detailed analytics on software usage, helping vendors understand customer behavior, identify potential compliance issues, and optimize licensing strategies for better monetization.
Revenue Protection: By reducing unauthorized use, DRM helps vendors capture more value from their intellectual property.
Flexible Monetization: DRM enables a wide range of business models, from pay-per-use to feature-based licensing, supporting tiered pricing and targeted upsells.
Global Compliance: DRM helps vendors enforce territorial restrictions and comply with international licensing agreements.
Data Security: Protects both the software and sensitive user data through encryption and access controls.
While DRM is essential for protecting software, it can introduce friction for legitimate users if not implemented thoughtfully. Common concerns include:
Device migration issues (difficulty transferring licenses to new hardware)
Access problems if DRM servers go offline
Potential privacy concerns due to usage tracking
Modern DRM solutions strive to balance robust protection with user convenience, offering cloud-based license management, seamless activation, and clear communication about usage rights.
Choose Flexible, Scalable Solutions: Look for DRM platforms that support multiple licensing models and can scale with your business needs.
Integrate with Licensing Systems: Combine DRM with robust software license management for granular control and automation.
Prioritize User Experience: Minimize friction by enabling easy activation, self-service license transfers, and transparent communication.
Monitor and Adapt: Use analytics to understand usage patterns, detect anomalies, and refine your protection and monetization strategies.
Stay Updated: Continuously update DRM mechanisms to address new threats, virtualization environments, and evolving piracy tactics.
Effective DRM is a cornerstone of modern software business. It protects intellectual property, supports innovative licensing and monetization strategies, and helps build trust with both customers and partners. As threats evolve and software delivery models diversify, the role of DRM in software will only become more central—provided it is implemented with a focus on both security and user experience.
Software activation for SaaS (Software as a Service) platforms fundamentally differs from traditional software activation methods that rely on product keys or local installations. In SaaS, activation is a cloud-driven, identity-based process focused on verifying user rights, enabling access, and ensuring compliance with subscription terms.
Key Steps in SaaS Software Activation:
User Account Creation and Verification: Activation begins when a user signs up for the SaaS product. The user provides an email address or other credentials verified through a confirmation email or multi-factor authentication.
License Assignment and Entitlement: After verification, the SaaS platform assigns entitlements based on the user's subscription or purchase. These entitlements control which features, modules, or service tiers the user can access.
Cloud-Based Validation: SaaS platforms validate access through cloud services rather than product keys. During each login or application access, the system checks user credentials against the vendor's licensing system. This ensures only authorized users can access the service, with entitlements that can be updated or revoked instantly.
Ongoing Compliance and Periodic Checks: SaaS applications regularly verify subscription status through the vendor's cloud licensing service. For example, Microsoft 365 Apps need an internet connection at least once every 30 days to stay activated; otherwise, they enter reduced functionality mode. This enables dynamic license management, including automatic deactivation when subscriptions expire or users leave.
Seamless User Experience: Modern SaaS activation is invisible and smooth for legitimate users. There's no need to manage product keys or manual activations. Access links directly to the user's identity, with subscription changes reflecting immediately in access rights.
Advanced Features in SaaS Activation:
Device and Usage Limits: SaaS licenses typically set limits on device or user access. The platform monitors installations and usage, automatically deactivating the oldest device when limits are reached.
Progressive Onboarding and Feature Unlocking: SaaS activation integrates with onboarding. As users complete important tasks (like connecting accounts or importing data), the platform gradually unlocks features, helping users discover the product's value.
Real-Time Updates and Revocation: With cloud-based entitlement management, SaaS vendors can instantly modify or revoke access when subscriptions change, improving security and compliance.
Summary Table: SaaS vs. Traditional Software Activation
Method
Cloud-based, identity-driven
Product key or local activation
User Experience
Seamless, no manual codes
Manual entry of codes
License Management
Real-time, centralized, flexible
Static, device-bound
Compliance Enforcement
Ongoing, automatic
One-time, user-dependent
Revocation/Updates
Instant, cloud-controlled
Manual, often requires user action
In summary:
SaaS software activation is a cloud-based, user-centric process that verifies entitlements through digital identity, manages access in real time, and ensures compliance with licensing terms—delivering a seamless user experience and robust control for vendors.
Yes, in many cases, you can transfer your software activation to another user or device. Still, the process and eligibility depend on the license type and the software provider's policies.
Key Points on Software Activation Transfer:
License Type Matters:
Retail and Subscription Licenses: These are often transferable. For example, subscription-based software like Microsoft 365 or Adobe Creative Cloud allows you to deactivate the license on your old device and reactivate it on a new one, usually by signing into your account.
OEM (Original Equipment Manufacturer) Licenses: Typically, these are tied to the original hardware and cannot be transferred to another device or user.
Volume Licenses: These are used by organizations and may allow reassignment through a management portal, but the process is controlled by IT administrators.
General Transfer Process:
Deactivate on the Old Device: Most software requires you to deactivate or sign out of the license on your current device before activating it elsewhere.
Uninstall (if required): Some vendors recommend uninstalling the software from the old device to avoid conflicts.
Install on the New Device: Download and install the software on the new device.
Reactivate: Enter your product key or sign in with your account to reactivate the software on the new device.
Verify Activation: Ensure the software is fully functional and licensed on the new device.
Important Considerations:
Always review the End User License Agreement (EULA) or support documentation to confirm if your license type is transferable and to understand any restrictions or fees.
Some licenses, such as OEM or certain discounted versions, are non-transferable and are permanently tied to the original device.
For enterprise or volume licenses, consult your IT department or license administrator for proper transfer procedures.
In summary:
Transferring software activation is often possible with retail, subscription, or volume licenses, provided you follow the proper deactivation and reactivation steps. Always check your license terms and vendor guidelines to ensure compliance and avoid activation issues.
A proprietary software license is a legal agreement used by software developers and companies to assert ownership over their software and control how it is used, distributed, and monetized. Unlike open-source licenses, which allow users to freely access, modify, and share source code, proprietary licenses restrict these rights and keep the source code confidential. The primary goal is to enable commercialisation by ensuring only authorized, paying users can access and use the software.
When you write new software, you automatically own the copyright, but a proprietary license provides the legal framework to enforce your rights and monetize your product. All commercially available software is distributed under some form of proprietary license, as simple copyright alone does not provide sufficient protection or control.
Ownership and Control: The software creator or publisher retains full rights over the software, including its code, features, and distribution.
Restricted Access: Users are granted a license to use the software under specific terms, but cannot view, modify, or redistribute the source code.
Monetization: Licenses are sold or leased, often requiring payment—either as a one-time fee (perpetual), a recurring subscription, or other models.
Legal Protection: The license agreement (often called an End User License Agreement, or EULA) outlines permitted uses, prohibited actions, and the consequences of violations.
Perpetual License: Allows indefinite use of a specific software version after a one-time payment, but may not include updates or support.
Subscription License: Provides access to the software for a limited period (monthly or annually), usually including updates and support as long as the subscription is active.
Volume License: Designed for organizations needing multiple installations, offering centralized management and cost savings.
Named User License: Tied to a specific individual, allowing use on multiple devices by that user.
Floating License: Shared among a group, allowing a limited number of users to access the software simultaneously.
Usage Limits: Restrictions on the number of installations, devices, or users.
Copying and Distribution: Prohibitions on sharing, copying, or redistributing the software beyond what is allowed for backup or archival purposes.
Modification and Reverse Engineering: Users are barred from decompiling, modifying, or reverse-engineering the software.
Transferability: Licenses are often non-transferable and cannot be resold or sublicensed without the vendor's permission.
Compliance and Auditing: Vendors may require users to demonstrate compliance and may audit usage.
Intellectual Property Protection: The license asserts the vendor's rights over the software, including copyrights, patents, and trademarks.
Proprietary software is closed-source, with strict usage and distribution restrictions. Users pay for the right to use the software under defined conditions, but do not own or control it.
Open-source software is publicly available, allowing anyone to view, modify, and distribute the code, often under licenses that promote collaboration and transparency.
Well-known examples of proprietary software include Microsoft Windows, Adobe Photoshop, MacOS, Microsoft Office, and iTunes. These products are distributed under proprietary licenses that strictly regulate how they can be used and shared.
Failure to comply with proprietary software licenses can result in legal action, financial penalties, or loss of access to the software. Organizations should carefully review license terms, ensure proper tracking of software usage, and maintain documentation to demonstrate compliance.
A proprietary software license is essential for software developers and companies seeking to commercialize their products, protect their intellectual property, and maintain control over distribution and usage. Understanding the terms, restrictions, and obligations of these licenses is critical for both vendors and users to ensure legal and ethical use of software.
Node-locked licensing is a widely used method for controlling software usage by tying a software license to a specific device—commonly referred to as a "node". This approach ensures that the licensed software can only be run on that particular device, which may be a computer, mobile device, or even an Internet of Things (IoT) device.
In this model, the license is paired with a unique hardware ID or "device fingerprint" that identifies the specific machine authorized to use the software. This makes node-locked licensing an effective way for software vendors to ensure only authorized, typically paying, customers can access and use their software.
Node-locked licenses are also known as single use, device, named host, machine-based, or anchored licenses.
License Binding: During installation or activation, the software generates or requests a unique hardware identifier (such as a MAC address, CPU ID, or other device fingerprint).
Activation: The license is activated and bound to this unique identifier, allowing the software to run only on that device.
Enforcement: If the software is copied to another device, it will not run unless a new license is purchased or the license is officially transferred.
Transferability: Some node-locked systems allow users to deactivate the license on one device and transfer it to another, but this is usually controlled and limited to prevent abuse.
Security
Ties the license to a specific device, reducing unauthorized use and piracy.
Simplicity
Straightforward to implement and manage for single-user or single-device scenarios.
Flexibility
Can be combined with other models (e.g., perpetual, timed, or subscription-based licenses).
Offline Use
Once activated, node-locked licenses can often be used without a continuous internet connection.
Support
Unique device identifiers simplify troubleshooting and support.
Lack of Portability: Node-locked licenses are not ideal for users who frequently switch devices or need to use the software across multiple machines.
No Network Sharing: These licenses cannot be shared by multiple users on a network or used in environments like thin clients or remote desktops.
Re-hosting: License transfer to a new device may require vendor approval or a formal deactivation process.
Device Failure: If the licensed device fails, users may need to contact support to reactivate the license on a replacement device.
Tied to a single device
Shared across multiple devices/users
Ideal for dedicated users
Ideal for teams or networked users
No concurrent usage limits
Limits on simultaneous users
Simple management
Requires license server or management
Node-locked licenses are best suited for:
Single-user, single-device scenarios
Environments where security and control are paramount
Software used offline or in remote locations
Applications where license sharing is not required
Use secure device fingerprinting to prevent spoofing.
Allow controlled license transfer or deactivation for user flexibility.
Provide clear documentation and responsive support for license management.
Consider combining with other models for broader customer needs.
Node-locked licensing is a robust and secure way to control software usage, ensuring only authorized devices can run the software. While it offers simplicity and strong protection against unauthorized use, it may not be suitable for every scenario—especially where flexibility and device sharing are needed. Vendors should weigh these factors when choosing a licensing model for their software products.
Software activation is crucial in SaaS because it marks the point where new users experience the core value of a product, directly influencing user engagement, retention, and revenue growth. Activation is not just a technical process—it is a pivotal stage in the customer journey that determines whether users become loyal, paying customers or quickly churn.
Key Reasons Activation Matters in SaaS:
Drives User Engagement and Retention: Activation ensures users quickly understand and benefit from your product. When users reach their "aha moment"—the point where they realize how the software solves their problem—they're more likely to continue using it. This reduces churn and increases long-term engagement.
Boosts Conversion Rates: Activated users are more likely to convert from free trials to paid plans. When users see value early through a smooth activation process, they're more inclined to upgrade, generating recurring revenue for the business.
Measures Product Success: Activation is a key metric for SaaS growth. Companies with higher activation rates see significant increases in monthly recurring revenue and customer lifetime value. Even excellent products struggle to retain users without proper activation.
Reduces Friction and Improves Onboarding: Good activation strategies help users overcome common challenges. By guiding users through key actions and showing value quickly, SaaS businesses can improve user experience and satisfaction.
Enables Data-Driven Optimization: By tracking activation metrics, SaaS companies can spot bottlenecks, test improvements, and refine the onboarding process. This helps more users reach important milestones and get value from the product.
Summary Table: The Impact of Software Activation in SaaS
User Retention
Activated users are more likely to stay and use the product long-term
Conversion
Higher likelihood of free-to-paid upgrades
Revenue Growth
Increased activation leads to higher MRR and LTV
Reduced Churn
Early value realization decreases user drop-off
Product Improvement
Data on activation guides onboarding and feature enhancements
In summary:
Software activation in SaaS is essential because it connects new users to the product's value, drives engagement and conversions, and underpins the growth and sustainability of the business. Without a strong focus on activation, SaaS companies risk losing users before they ever see what makes the product valuable.
An Independent Software Vendor (ISV) is a business or individual that develops, markets, and sells software products for end users—either consumers or enterprises. Unlike software built for internal use (in-house software) or custom solutions for a single client, ISV software is designed for broader distribution and consumption by multiple customers.
ISVs are also known as software publishers. Their primary function is to create and distribute their own software, which always remains the property of the ISV and is licensed—not sold outright—to end users. This distinction separates ISVs from original equipment manufacturers (OEMs) and hardware vendors, who may also distribute software but typically focus on system-level or bundled applications.
Independence: ISVs operate independently from hardware or operating system manufacturers, focusing on software innovation and distribution.
Specialization: Many ISVs target specific industries or business verticals, offering niche solutions that platform vendors may not provide.
Innovation: ISVs are often at the forefront of technological advancements, rapidly adopting new technologies such as cloud computing, artificial intelligence, and SaaS delivery models.
Distribution: ISVs license their software through various models, including perpetual licenses, subscriptions, usage-based, and SaaS. Distribution channels include direct sales, online marketplaces, and partnerships with platform providers.
Support and Updates: ISVs typically provide ongoing support, maintenance, and updates to keep their products secure, reliable, and competitive.
ISVs vs. OEMs: ISVs focus on end-user applications, while OEMs typically provide system-level software bundled with hardware.
ISVs vs. Software Resellers: ISVs create and sell their own software, whereas resellers distribute software developed by others.
ISVs vs. In-House Developers: ISVs build for the external market, while in-house developers create software solely for their own organization's use.
ISVs range from small startups to global enterprises. Their products span a wide array of industries and use cases, such as:
Customer Relationship Management (CRM)
Enterprise Resource Planning (ERP)
Healthcare, finance, and retail applications
Specialized tools for real estate, logistics, analytics, and more
Major platform providers—like Microsoft, IBM, Google, Oracle, Apple, AWS, and Salesforce—actively support ISVs through business partner and certification programs. These partnerships help ensure compatibility, expand software ecosystems, and drive mutual business growth.
With the rise of cloud computing, virtualization, and SaaS, ISVs have shifted from traditional software delivery to offering cloud-based solutions and selling through cloud marketplaces such as AWS, Microsoft Azure, and Salesforce AppExchange. This transformation has enabled greater scalability, flexibility, and reach for ISVs and their customers.
ISVs are crucial in filling market gaps, providing industry-specific solutions, and driving digital transformation for businesses of all sizes. Their agility allows them to quickly adapt to emerging customer needs and integrate the latest technologies.
To thrive, ISVs must:
Continuously innovate and update their products
Protect and monetize their intellectual property with robust licensing and software monetization strategies
Build strong relationships with platform providers and participate in partner programs
Deliver reliable support and maintain customer trust
ISVs are fundamental to the software industry, powering innovation and delivering specialized solutions across every sector. Whether you're a developer, business leader, or IT buyer, understanding the role of ISVs helps you navigate the software landscape and leverage the best solutions for your needs.
Software license compliance ensures that all software used within an organization is utilized strictly according to the terms and conditions set by the software developer or vendor in the licensing agreement. This means not breaching any usage, distribution, modification, or installation restrictions specified in the license. In essence, compliance requires that organizations only use software they are legally entitled to, in the manner and scope defined by the license agreement.
Key Aspects of Software License Compliance:
Legal Foundation: A software license is a legally binding agreement between the software vendor and the user. Compliance means adhering to all the rules and limitations outlined in this agreement, including how the software can be used, how many copies may be installed, and who may access it.
Ownership and Rights: Typically, the software developer or vendor retains ownership of the software. The end-user receives the right to use the software under specific conditions but does not own or have the right to redistribute or modify it unless explicitly allowed.
Scope of Compliance:
Installations: The number of software installations and users must not exceed what is permitted by the license.
Usage: Only the features and functionalities covered by the license may be used.
Version Control: Using software versions not covered by the license or assuming rights based on previous versions can lead to non-compliance.
Geographic or Organizational Limits: Some licenses restrict usage to specific locations or business units.
Common Causes of Non-Compliance:
Unauthorized Installations: Installing software on more devices or for more users than licensed is a frequent breach, often referred to as software piracy.
Accidental Violations: Misunderstandings about license terms, mergers and acquisitions, or administrative errors can lead to accidental non-compliance.
Lack of Record-Keeping: Failure to maintain accurate records of software purchases, installations, and usage increases the risk of non-compliance.
Risks and Consequences:
Legal and Financial Penalties: Non-compliance can result in audits, "true-up" charges, fines, or even lawsuits. Over half of software audits uncover non-compliance, with significant financial repercussions for organizations.
Reputational Damage: Being found non-compliant can harm an organization's reputation and relationships with vendors and customers.
Operational Disruption: Audits and remediation efforts can disrupt business operations.
Best Practices for Ensuring Compliance:
Understand License Terms: Review and fully understand the conditions of each software license agreement before deployment.
Inventory and Track Usage: Maintain a comprehensive inventory of all software assets and regularly compare actual usage to licensed entitlements.
Internal Audits: Conduct regular internal audits to identify and address compliance gaps before external audits occur.
Use Compliance Management Tools: Implement software asset management (SAM) or license management solutions to automate tracking, alerts, and reporting.
Educate Employees: Train staff on the importance of compliance and the specifics of your organization's software policies.
Vendor Communication: Maintain open communication with software vendors regarding renewals, changes in usage, and compliance requirements.
Who is Responsible?
While software license compliance is often seen as a CIO or IT issue, ultimate responsibility lies with company directors, as non-compliance can have significant commercial and legal implications for the entire organization.
Legal Agreement
Adherence to all terms in the software license agreement
Usage Restrictions
Only using software as permitted (installations, users, features, locations, etc.)
Ownership
Software remains the property of the developer/vendor; end-users have usage rights only
Record-Keeping
Maintain accurate records of licenses owned and software deployed
Auditing
Regular internal and external audits to verify compliance
Risk Management
Avoid legal, financial, and reputational risks by ensuring compliance
Software license compliance is a critical and ongoing business process that protects organizations from legal, financial, and operational risks. It requires a thorough understanding of license agreements, diligent tracking of software assets, regular audits, and proactive management to ensure all software is used strictly within the boundaries set by the vendor or developer.
Perpetual software licensing is the traditional model in which customers pay a one-time fee to use a specific version of the software indefinitely. This approach provides long-term access and a sense of ownership, with no recurring payments for the core product.
Predictable, upfront costs for the software
Long-term stability and autonomy over update schedules
No ongoing subscription fees for the main product
However, support, maintenance, and upgrades may require additional fees.
Vendors gain upfront cash flow.
Customers secure long-term use and control over their software environment.
Stable, long-term software needs
Preference for capital expenditure over operational expenses
Environments where frequent updates are less critical
Integration with cloud services for perpetual licenses
Hybrid models combining perpetual and subscription features
Enhanced support and upgrade paths for perpetual license holders
Assess your budget cycle, technology change rate, and IT strategy
Perpetual licensing is best for organizations needing long-term, stable software access
Software piracy is the illegal copying, distribution, or use of software that is protected by copyright laws. It constitutes the act of stealing software by violating the terms set by the software's copyright holder, including unauthorized reproduction, sharing, or installation of the software without proper licensing or permission.
Forms of Software Piracy:
Unauthorized Copying: Making and using more copies of software than the license permits, often referred to as "end-user" piracy.
Cracking: Gaining illegal access to protected software by bypassing security measures.
Counterfeit Distribution: Reproducing and distributing unauthorized or fake versions of software, often over the internet.
Softlifting: Sharing software with others who are not licensed to use it, such as giving a friend a copy to install.
Online Sharing: Distributing pirated software through peer-to-peer (P2P) networks, online auction sites, or other digital channels.
Why Software Piracy is a Crime:
Piracy infringes on the intellectual property rights of the software creator.
It is considered theft because it deprives the rightful owner of revenue and control over their product.
Legal consequences can include fines and, in severe cases, criminal charges.
Consequences of Software Piracy:
For Software Vendors: Loss of revenue, increased costs for anti-piracy measures, and potential damage to brand reputation.
For Users: Legal risks, exposure to malware or compromised software, and lack of access to updates or support.
Anti-Piracy Measures:
Encryption and DRM: Protecting software with encryption and digital rights management to prevent unauthorized use.
Hardware Keys/Dongles: Requiring physical devices for software activation to ensure only legitimate users can access the software.
User Authentication: Implementing multi-factor authentication, single sign-on, or biometric verification to restrict access.
Digital Watermarking: Embedding invisible markers in software to trace pirated copies back to their source.
Real-Time Monitoring: Using software tools to monitor usage and detect unauthorized distribution or access.
AI and Machine Learning: Employing advanced analytics to identify patterns of piracy and respond to new threats.
Role in Software Monetization:
Preventing piracy is a key component of software monetization strategies, as it ensures that only paying customers can access the product, thereby maximizing revenue and protecting intellectual property.
Software piracy undermines both the legal and financial foundations of the software industry. By understanding its forms and implementing robust anti-piracy measures, software vendors can better protect their products, ensure compliance, and support sustainable business growth.
Account-Based Licensing is a modern, user-centric approach that replaces traditional license codes with a username-and-password login system. Users access software through credential-based login, centralizing entitlements and simplifying management.
Key Features:
Streamlines user experience.
Reduces support issues related to license codes.
Enhances control over software access and usage.
Benefits:
Aligns with SaaS and mobile app user expectations.
Potentially increases adoption and customer satisfaction.
Trends:
Integration with single sign-on (SSO) and biometric authentication.
AI-driven entitlement management and analytics.
Expansion to IoT and cross-platform solutions.
Account-Based Licensing is best for organizations seeking to modernize distribution, improve user experience, and reduce management complexity.
Software licensing that tracks what your customers use enables you to adopt a new pay-as-you-use style of licensing to police what customers use. One of the leading modern ways to sell and monetize your software is to offer it using Usage-Based Licensing, charging your customers for what they use and billing them pre- or post-usage.
Software vendors are excited about a usage-based or metered approach to monetizing software. This approach perfectly complements entitlement management in several ways.
When you sell an entitlement to a customer, you're defining what they can do—what features, abilities, and capacities will be unlocked in the software based on their purchased license. This allows you to implement various business models like perpetual, floating, and others. However, this doesn't account for how customers actually use the software. For example, if you sold them 100 concurrent seats, how many are they actually using?
We allow you to bring usage data back into the cloud for analysis as part of entitlement management and license enforcement. From a usage-based pricing standpoint, we can map that usage data against a billing model, creating a hybrid between an entitlement (defining capabilities) and usage tracking (determining billing).
Here's an example: You might sell a one-year subscription for 100 seats and allow an overdraft capacity of 20 or 30 additional seats. While you monetize the base subscription for those 100 seats, you'll also track the usage of the overdraft seats. This usage data flows against a pre-agreed business model—perhaps charging based on peak usage or charging for any day that exceeds the 100 purchased seats.
You can also use this information to understand usage patterns without immediate billing. Instead, you might consider this data during renewal discussions to configure their license more appropriately. This marriage of entitlement management, usage tracking, and billing creates a comprehensive usage-based or metered approach to monetization.
You may commonly use Usage-Based Licensing in conjunction with Subscription-Based Licensing. For example, you may wish to sell a Monthly Subscription that includes a preset amount of usage, then offer customers the ability to purchase additional usage when they exceed their initial quota.
Zentitle Usage-Based Licensing works by tracking usage for specific features belonging to a License Code. Setting initial usage limits is easy, and it is equally simple to adjust these limits as required using simple automated web-service calls or manually in the Zentitle Licensing user interface.
What's great about Zentitle's Usage-Based Licensing is that it can be used in conjunction with many other forms of our licensing.
For example, you might use our Concurrent Licensing so that only a limited number of users within a larger total of users can use your software at once. This can even be done with one license code. So, you can effectively have a group of users all sharing the same usage limits.
Another example: In conjunction with our Account-Based Licensing, you can have your users log in using their Email Address and Password to use your software (they don’t need to be exposed to conventional License Codes) and can use whatever they pay for.
Common configurations, such as subscriptions to differently priced tiered offerings, including pre-defined usage limits, are as easy to deploy as pure and simple Pay-as-you-go Models.
In short, usage-based licensing provides extremely flexible ways for this modern licensing method to work for you.
Zentitle enables you to adopt proven software licensing models that increase revenue while simplifying license management.
With Zentitle Cloud-Based Licensing, implementing revenue-boosting software licensing models is quick and straightforward. It's the most effective way for software vendors to grow sales and revenue.
These licensing models can work together, simplifying complex use cases that are easy to describe but typically difficult to implement.
One of the real benefits of adopting the Zentitle platform as you bring your products to market is the ability to separate the business model from the application implementation itself. You instrument your application once, then can take it to market with various business models, such as feature-based licensing that lets you enable or disable specific capabilities, modules, and components per license.
The platform supports all types of time-based licenses: one-month subscriptions, one-year subscriptions, or licenses that expire on a specific date, like December 31st, 2025. You can implement any date-based metric you need.
You can also offer perpetual or non-expiring licenses with optional maintenance contracts. The entitlement tracks when maintenance contracts end, allowing you to build logic into your application and only allow software updates for licenses within their maintenance window.
For version-based licensing, you have two options. First, you could require separate licenses for each product version (version 2, version 3, etc.). However, we recommend defining a valid range of versions within the entitlement. Start with a 2.x line, then as customers upgrade to 3.x or 4.x versions, they keep the same license but update their attributes to include the new version ranges.
We fully support usage-based, consumption-based, and software-as-a-service models through our consumption tokens and other capabilities. This makes it easy to track resource usage over time within the license.
From a capacity standpoint, you can use entitlement attributes to set specific limits. For example, a lower-cost edition might manage up to 10 widgets, a mid-tier up to 50 widgets, and an enterprise edition could offer unlimited widget management. You can include as many of these attributes as needed.
We also support named user models. You can set up a license for 10 specific users based on identity and allow your end customer to manage their list of authorized users.
Similarly, we allow integration with identity-based systems to provide experiences like Adobe Creative Cloud or Office 365, where end customers activate seats using email addresses and passwords. We integrate with any OpenID-based identity platform—whether that's Auth0, Okta, Cognito, or Azure AD.
This provides additional benefits for end customers with their own identity provider (IdP). They can federate into these identity platforms, allowing single sign-on access to license rights.
We provide these capabilities for customers with ongoing internet connections, intermittent connectivity, or completely disconnected ("dark site") environments. This works for node-locked individual seat licenses and concurrent or network-based licensing models running in dark environments.
Across all these capabilities, you can monetize your application however you want, mixing and matching models without building dependencies into your core application. This means you can easily deploy new packages, offerings, and pricing without engineering changes.
This traditional "buy once, use forever" model is familiar to most users. While many software companies are moving away from this approach, Zentitle provides robust support, including Offline Activation. This ensures a hassle-free experience for end-users while reducing licensing-related support requests.
Today's consumers are increasingly comfortable with SaaS-style subscriptions. Zentitle's Cloud-Based Licensing makes it easy to implement subscription-based licensing for Desktop, Server, IoT, and Mobile software and desktop-SaaS hybrid solutions. Combined with Account-Based Licensing, this model shifts focus from license codes to users.
Simplify bulk licensing for your customers by restricting the number of active software copies permitted per license code. This allows business customers to purchase what they need while ensuring they only use what they're entitled to. The streamlined management system significantly reduces licensing support issues.
For business customers with multiple software instances, you can limit the number of users who can access specific features simultaneously. For example, while 10 users may run your software, only three can use a particular feature simultaneously.
Element Pools lets you manage resource access across multiple instances. For example, with 10 graphics workstations sharing 100 processing cores for rendering, each workstation can access the cores as needed. Still, total usage across all machines cannot exceed 100 cores at any time.
This modern licensing model tracks usage through Consumption Pools and Tokens. Whether you need usage-based contracts or want to offer pay-as-you-go or prepaid options, this model works seamlessly with our Subscription and account-based licensing.
Account-based licensing puts the user at the center, using email/username and password for entitlements. While common in mobile and SaaS applications, this approach works for Desktop, Server, and SaaS-Desktop Hybrid solutions. It's compatible with all other Zentitle licensing types.
Set licenses to expire on specific dates and extend them as needed through the Licensing UI or API.
Control exactly which features each user can access through License Codes or Accounts. Go beyond simple on/off toggles with options like Concurrent Licensing, Consumption Licensing, or limited trial periods.
For software suites with multiple versions (Lite/Standard/Pro) or components (Word Processing/Spreadsheet/Presentation), ship everything in one binary and let Zentitle manage access control. This simplifies upgrades and reduces engineering complexity by minimizing the number of binaries to maintain.
For customers using software at sites without regular internet access, Zentitle offers flexible solutions. Our Network Licensing Server runs on your LAN to manage permissions across computers, devices, or users. Alternatively, our Network Relay Server provides DMZ access to cloud-based licensing.
Zentitle Offline Licensing supports most licensing models with simple, hassle-free activation when internet access is unavailable or restricted. The customizable portal maintains your brand identity.
Zentitle supports multiple platforms to maximize licensing benefits for hardware companies with software-driven products. From initial provisioning to customer deployment, our Hardware Licensing provides control and monetization opportunities. Customer upgrades take effect with a simple reboot.
Track maintenance contracts, whether sold separately or included with initial software purchases.
Zentitle Licensing works across Windows, Mac, Linux, Android, ARM, Java, FreeBSD and more. Contact us about specific platform requirements.
Zentitle Licensing includes comprehensive trial capabilities. Customize trial experiences from time-limited access to feature restrictions, and showcase new features through upgrade trials.
Zentitle Cloud-Based Licensing simplifies multi-user customer management. Replace individual license codes with efficient concurrent licensing and multi-activation licenses.
Buy: Purchasing a solution like Nalpeiron’s Zentitle allows your team to focus on your core product rather than diverting resources to develop and maintain a licensing system. This is ideal if licensing is not a strategic differentiator for your business.
Build: Developing in-house may make sense if licensing is integral to your competitive advantage or aligns with your core expertise.
Buy: Ready-made platforms like Zentitle are designed to be deployed quickly, often within days, enabling faster time-to-market for your products.
Build: Building in-house can take months or even years, delaying product launches and potentially losing market opportunities.
Buy: While buying involves upfront licensing fees, it typically reduces long-term costs associated with development, maintenance, and compliance updates.
Build: Building in-house can incur significant costs in development, ongoing maintenance, and ensuring compliance with evolving standards. These costs can escalate if the system requires frequent updates or scaling.
Buy: Commercial solutions like Zentitle are built to scale with your business and adapt to changing needs without requiring extensive rework.
Build: Custom-built systems may struggle to scale efficiently or adapt to new requirements unless significant resources are allocated for continuous improvement.
Buy: Off-the-shelf solutions often have built-in integrations for common platforms and APIs, simplifying deployment into existing ecosystems.
Build: Custom solutions may require additional effort to integrate with existing systems, especially if the architecture is complex or outdated.
Buy: Vendors like Nalpeiron handle ongoing updates, compliance requirements, and support, reducing the burden on your internal teams.
Build: Maintaining compliance with licensing standards and updating the system requires dedicated resources and expertise.
Entitlements track what your customers have purchased and all changes through the lifecycle.
In the context of software licensing, entitlement refers to the specific rights and permissions that a customer has to use a particular software product. An entitlement is essentially a record of what a customer has purchased, determining what they can do with the software.
Entitlements can include a wide range of permissions and restrictions, depending on the specific licensing agreement. Some common examples of entitlements include:
The number of users or devices that are allowed to access the software
The specific features or modules that are included in the license
The geographic location or territory where the software can be used
The duration of the license, including start and end dates
The level of technical support that is included with the license
Any restrictions on how the software can be used or distributed
Entitlement management is an important part of software licensing, as it helps ensure that customers are using the software in compliance with the licensing agreement. By tracking entitlements, software vendors can ensure that customers are only using the software within the limits of their license, which helps prevent misuse and piracy.
Using our Dynamic Entitlements, the complexity of license entitlement updates is completely removed for you and your customers. You can easily upgrade, downgrade, or change features on demand, without the end-user having to do anything to use what they now own. Legacy licensing platforms often force your customers to install a brand new license when they want to upgrade or modify their rights, unnecessarily overwhelming them with complex license file management, not with Zentitle.
Zentitle enables you to provision your customers (B2B, B2C, B2B2C), manage their rights, with simple license activation and deactivation.
Any environment
Easily deploy on-premises, in networks, to SaaS, or with embedded devices and IoT
Any business model
Subscription, Concurrent, Consumption, Feature-Based models, and more
Account-based licensing
Log in and use for your customers, witha username and password
Frictionless for end-users
Licensing tasks are so simple, support tickets drop by up to 60%
Maximize revenue opportunities by understanding exactly how your customers use their purchased plans and licenses. This will allow you to target and grow accounts with the greatest sales potential. With these insights, you can reduce churn, maximize renewal rates, and identify accounts ripe for cross-sell and upsell opportunities.
Improve development
Once you know how your customers use your software, you can make informed decisions when developing your product. By knowing what users use and what they don’t, avoid wasting effort on low-value features and concentrate on delivering functionality that will delight existing customers and draw new ones in.
Offline Licensing enables software access and management in environments where internet connectivity is limited, unavailable, or restricted. This model allows software to be properly licensed and activated without a direct online connection, supporting a wide range of user scenarios.
Activation and license verification can be done via phone, email, or offline activation portals.
License files can be securely transferred and used for activation in air-gapped or high-security environments.
Cryptographic signing and encryption ensure license integrity and authenticity even without internet access.
Serves customers in remote or high-security locations
Maintains licensing control and compliance without needing constant connectivity
Supports a variety of activation methods tailored to the customer’s environment
Blockchain for decentralized license verification
AI-driven predictive activation for better offline preparedness
Advanced cryptographic schemes for enhanced security
Customers operate in remote, regulated, or high-security environments
Internet access is unreliable or strictly controlled
Need for secure, tamper-proof license management
Evaluate your users’ working conditions and internet access frequency
Assess your capacity to manage multiple activation methods
Hardware Licensing monetizes and controls hardware products with embedded software. Vendors use secure licensing mechanisms to control device functionality, allowing a single hardware platform to be configured into multiple product tiers via software.
Key Features:
Enables instant upgrades and feature activations without hardware changes.
Reduces manufacturing complexity.
Benefits:
Increases revenue potential and product flexibility.
Supports dynamic product offerings and responsive upgrades.
Trends:
AI/ML-driven dynamic licensing.
Blockchain for secure, decentralized license management.
Real-time control is enabled by improved connectivity.
Hardware licensing is ideal for hardware with significant software components, such as IoT devices, as it provides flexibility and a streamlined inventory.
In software licensing, a License Pool represents a fundamental concept within floating licensing or concurrent licensing models. It functions as a centralized repository containing a predetermined quantity of available licenses that end-users throughout an organization can dynamically check out and utilize based on their immediate requirements.
The process begins when an individual attempts to launch a software application that implements this licensing model. At that moment, the application automatically initiates a request to the License Pool for an available license. If the pool contains an unused license, that specific license is temporarily checked out and assigned to the user, allowing the application to initialize and become fully operational.
However, if all licenses within the pool have already been allocated to other users, the application will be unable to start, displaying an appropriate notification to the user. The License Pool maintains its dynamic nature through an automated return mechanism - licenses become available again for redistribution either when current users terminate their application sessions, thereby releasing their licenses back to the pool, or when the allocated licenses reach their predetermined expiration time, automatically returning to the available state for other users to access.
Subscription-based licensing has transformed the software industry, offering a flexible and cost-effective way to access powerful tools and applications. Instead of a one-time purchase, users pay a recurring fee, typically monthly or annually, for continued access. This model ensures customers have the latest features and updates as long as their subscription remains active.
The rise of cloud computing and SaaS (Software-as-a-Service) has accelerated the adoption of this model. Benefits include:
Lower upfront costs
Easier scalability
Continuous access to updates and new features
For vendors, subscription licensing provides predictable, recurring revenue and fosters ongoing customer relationships. This encourages continuous product improvement and innovation, as vendors must deliver ongoing value to retain subscribers.
Access to the latest software versions and updates
Flexible pricing and scaling options
Ongoing support and enhancements included
Integration of AI and machine learning for personalized experiences and predictive insights
Hybrid models combining subscription and perpetual licensing (e.g., converting subscriptions to perpetual licenses after a period)
Expansion to hardware-software bundles, especially with IoT
Subscription licenses are ideal if you:
Want always-updated software
Need to scale usage up
Prefer operational expenses over capital investment
Review your budget cycle, pace of technological change, and IT infrastructure
Subscription pricing supports customer retention and predictable revenue
Software license keys function as critical components within sophisticated copy protection schemes meticulously designed to regulate and control software access across various platforms and systems. When users successfully purchase a software license through authorized channels, they receive a unique alphanumeric key as their digital authorization credential, enabling them to properly install, authenticate, and fully utilize the software on their designated systems.
From a developer's perspective, these carefully crafted license keys are a crucial protective mechanism to help prevent unauthorized copying, illegal sharing, and digital piracy of their valuable intellectual property and meticulously developed software products.
License keys are systematically generated through sophisticated secure algorithms and delivered electronically to users immediately following payment confirmation and explicit acceptance of the comprehensive End-User License Agreement terms and conditions. This automated process ensures immediate access while maintaining security protocols.
A software license key, also commonly referred to as a product key or activation code, functions as a sophisticated digital verification system that authenticates and validates the legitimacy of a program installation. The key consists of a carefully constructed, unique string of numbers and characters, typically arranged in a specific pattern to prevent errors and ensure proper validation.
In contemporary software systems, most applications implement mandatory online activation protocols and robust verification mechanisms to ensure that individual license keys cannot be simultaneously utilized across multiple computer systems or devices, maintaining the integrity of the licensing system.
Alternatively, some software developers use a license dongle to implement a more advanced approach. This specialized physical hardware device connects directly to the computer through standard ports such as USB or parallel interfaces. One significant advantage of these hardware-based authentication keys is their ability to function independently without requiring an active internet connection for validation, making them particularly suitable for secure environments or locations with limited connectivity.
Users are prompted to input their designated license key through a secure interface during the software installation process. This key functions as a sophisticated digital unlock mechanism, validating the installation through multiple authentication steps and enabling full access to the software's complete range of features and functionality upon successful verification.
While license keys represent a long-standing traditional method of controlling and managing software access in the digital ecosystem, they come with several notable drawbacks that affect both end users and software developers in significant and sometimes unexpected ways.
User Inconvenience: The management and maintenance of software license keys can prove particularly cumbersome and challenging for end-users, often resulting in a diminished overall user experience and increased frustration during installation, system migrations, or hardware upgrades.
Ineffectiveness in Preventing Piracy: Despite their intended purpose and sophisticated implementation, license keys frequently demonstrate limited effectiveness in preventing unauthorized software use or digital piracy, as determined individuals can potentially share, duplicate, or bypass these keys through various technical means and sophisticated circumvention techniques.
From the perspective of software vendors and developers, the ongoing administration and management of license key systems often represents an unnecessary operational burden that demands significant resources and could be better addressed through alternative solutions or more modern authentication methods.
Software license keys offer several essential and strategic benefits for both developers and users in the software ecosystem:
Revenue Protection: License keys help ensure software developers receive appropriate compensation for their intellectual property and development efforts by controlling product access through systematic verification processes.
Usage Tracking: Companies can comprehensively monitor and analyze how their software is deployed across different systems and organizations, enabling better resource allocation and development planning.
Version Control: License keys can help manage different software versions and feature sets, enabling sophisticated tiered pricing models and customized deployment options
Customer Support: Valid license keys make it easier to verify legitimate users when providing technical support and troubleshooting assistance, streamlining the support process.
Distribution Control: Publishers can effectively regulate software distribution channels and maintain better control over their intellectual property through systematic license management.
A software entitlement is the explicit right or set of permissions granted to a user, device, or organization to access and use specific software products, features, or services. These rights are typically defined by a contract, license agreement, or subscription plan, and are enforced through technical systems that manage, monitor, and control access according to the terms agreed upon between the software provider and the customer.
Core Elements of Software Entitlement:
Rights and Permissions: Software entitlements specify exactly what a user or organization can do with the software. This includes which features are accessible, how many users or devices can use the software, the duration of access, and any usage limits (such as number of API calls or storage capacity).
Assignment and Enforcement: Entitlements are assigned to users, machines, or groups, and are enforced by the software vendor through entitlement management systems. These systems ensure that only authorized users can access the software, and only within the boundaries defined by their entitlements.
Granularity: Entitlements can be highly granular, controlling access to individual features, modules, or service tiers within a product. For example, a basic plan might allow access to core features, while a premium plan unlocks advanced functionality.
Lifecycle Management: Entitlements are managed throughout their lifecycle, including issuance (when a customer purchases or subscribes), modification (upgrades, downgrades, or changes in user roles), and revocation (when access is rescinded due to non-payment, contract end, or policy violation).
Compliance and Monitoring: Entitlement management systems track usage in real time to ensure compliance with licensing agreements and prevent unauthorized use. This helps vendors maximize license compliance and minimize revenue leakage.
How Software Entitlements Work:
When a customer purchases software, the transaction is recorded and translated into specific entitlements—essentially, a detailed receipt of what the customer is allowed to access.
Entitlement management systems then enforce these rights, granting access to features, managing user counts, and monitoring usage to ensure compliance with contract terms.
For the end user, entitlements are typically invisible—they simply experience access to the features or services they have paid for. For the vendor, entitlements are a technical mechanism for controlling and tracking access.
Types of Software Entitlements:
Feature-based
Access to specific functionalities within the software (e.g., reporting, integrations).
Usage-based
Rights defined by usage limits (e.g., number of installations, API calls).
User/device-based
Rights assigned to specific users or devices (e.g., 10 users, 5 devices).
Time-based
Access for a defined period (e.g., annual subscription, perpetual license).
Support/updates entitlement
Rights to receive updates or technical support.
Key Benefits and Purposes:
Monetization: Enables flexible pricing and packaging strategies, such as tiered plans or add-ons, to drive revenue growth.
Security and Compliance: Ensures only authorized users have access, reducing the risk of license violations and unauthorized use.
Operational Efficiency: Automates access control, reducing manual intervention and administrative overhead.
Customer Experience: Allows customers to upgrade, downgrade, or customize their access easily, aligning software use with their needs.
Examples:
A company buys 50 licenses for a software product; the entitlement specifies which users or machines can use those licenses and what features they can access.
In a SaaS product, a "Pro" plan entitlement might unlock integrations and advanced analytics, while a "Basic" plan restricts users to core features.
Definition
Legal right to use software under defined terms
Specific permissions and access rights
Scope
Number of users/devices, installation rights
Features, usage limits, support, time, etc.
Enforcement
Legal agreement, sometimes technical controls
Technical enforcement via entitlement management
Flexibility
Generally fixed at purchase
Highly granular, can be updated or revoked
Visibility to user
Sometimes explicit (license keys)
Usually invisible, managed by vendor
A software entitlement is the mechanism by which software vendors define, assign, and enforce the rights and permissions that customers have to access and use their software. It is a foundational concept for modern software delivery, enabling flexible business models, ensuring compliance, and providing a tailored customer experience.
Element Pools Licensing is an advanced, flexible approach to software resource management. It enables control over specific resources (“elements”) across multiple software instances, ensuring optimal utilization and fair distribution.
Resources are defined as a pool of elements.
Software instances check out elements as needed and return them when done.
Dynamic allocation ensures resources are available where needed without exceeding licensed limits.
Granular control over resource usage
Aligns pricing with actual value delivered to customers
Optimizes resource allocation and expenditure
AI and machine learning for usage prediction and automated pool size optimization
Integration with cloud-based resources for flexible scaling
Management of distributed resources across edge computing environments
Resource-intensive applications with fluctuating usage patterns
Need for dynamic, efficient allocation across users or departments
Organizations seeking to align costs with actual resource consumption
Assess the variability of your resource needs and the number of software instances in use
Evaluate your ability to manage more complex licensing systems
Trial or Evaluation Licensing allows potential customers to experience software through time-limited or feature-restricted versions before purchase.
Key Features:
Flexible trial configurations: time-limited, feature-restricted, or gradual unlocking.
Drives adoption and sales by providing hands-on experience.
Benefits:
Low-risk entry for users.
Generates leads and increases conversion rates.
Trends:
AI-driven personalized trial experiences.
Progressive trials unlock features based on engagement.
Usage-based trials.
Trial Licensing is ideal for expanding the user base and showcasing product value.
Feature-Based Licensing offers granular control over which software features are available to each user or license holder, enabling tailored product offerings.
Key Features:
Enables/disables features per license code or user account.
Supports sophisticated schemes like concurrent usage, consumption-based access, or time-limited trials.
Benefits:
Facilitates diverse product offerings and upsell strategies.
Allows dynamic adjustment of entitlements.
Trends:
AI/ML for adaptive licensing.
Usage-based feature licensing.
Management across integrated applications and IoT.
Feature-Based Licensing is ideal for complex software with diverse user needs and sophisticated pricing strategies.
Floating Feature Licensing provides granular control over feature accessibility, limiting the number of users who can access specific features simultaneously across multiple software instances.
Key Features:
Sets caps on concurrent usage of particular features.
Optimizes software investments for resource-intensive features.
Benefits:
Enables tiered pricing and nuanced monetization.
Aligns feature access with actual usage patterns.
Trends:
AI/ML for usage predictions and automated optimization.
Hybrid models with subscription-based pricing.
Modular and microservices-based management.
Floating Feature Licensing is best for organizations with diverse user needs and those optimizing costs for specialized features.
Multi-Platform Licensing enables consistent management and control of software access across various operating systems and devices.
Key Features:
Uniform licensing policies for Windows, Mac, Linux, ARM, Java, mobile, and IoT devices.
Expands market reach and simplifies product management.
Benefits:
Seamless user experience across platforms.
Flexibility in deployment and usage.
Trends:
Cloud services for cross-platform license management.
Containerization for simplified deployment.
Support for edge computing and IoT.
Multi-Platform Licensing is essential for vendors targeting diverse technological environments and broad user bases.
Have your end-users log in and use the software without needing license codes.
Account-based Licensing makes the user themselves the identifier for their entitlements: Email Address and Password. There are no license codes to send back and forth, nothing for the user to remember to keep, and nothing to stress out down the line when they need it again and can't remember where they saved it. When you use Zentitle Account-Based Licensing, your customers get the same user-centric experience that they get nowadays from Adobe, Microsoft, or all those SaaS Services like Dropbox, Evernote, Google, and iCloud. Users can roam from device to device, only ever needing to remember their email address and password (any username is supported, email address is most common). Most of all, though, Account-Based Licensing is incredibly flexible. You can use it in conjunction with pretty much all of our Licensing Models to deliver and control entitlements exactly as you want.
Subscriptions, Usage Based, Feature Based, and Concurrent models, and much, much more are all possible. With Zentitle, we don't restrict you by only allowing simple fixed use cases that in real life are restrictive, plus you get a truly modern platform with the assurance of Nalpeiron's 20 years in leading in the software licensing industry. It works extremely effectively if you sell to business customers, too. Our comprehensive license models, along with Dynamic Entitlements and Account-Based Licensing, make managing your customer entitlements much easier and, importantly, much more hassle-free for the customers themselves. Zentitle provides an End-User Portal for you so that your end-users or even your multi-user business customers have just what they need to get full insight into the software they own and how they use it.
The End User Portal works hand-in-hand with Account-Based Licensing, giving you everything you need to support your customer base with a high degree of self-service, which in turn minimizes your operational support overheads. Of course, the End User Portal is brandable to ensure brand continuity. Account-Based Licensing easily integrates with your own approach to managing user identities, from companies such as Auth0, Okta, etc. - allowing you to have a single sign-on identity that can be used across license activations for on-premise software, logging in to SaaS offerings, entering support tickets, accessing customer portals, forums, downloads, and the like. This enables a ‘Best of Breed’ approach that leverages the power and flexibility of the Zentitle platform in combination with standards-based identity management platforms (such as those supporting OpenID Connect, OAuth2, SAML2, etc.) For those who don’t need the full flexibility of a separate dedicated identity management solution, Zentitle can provide a central point of control for end-user identities for a similar modern experience of ‘login and use’.
Account-based licensing doesn't have to center around an individual person. It can be used to great effect in many commercial and industrial applications where a device is not operating as a person. If you've been wondering about how you can use Account-Based Licensing in business, industrial, commercial, or hardware/software infrastructure deployment, then reach out and ask about the use cases you are thinking of.
Multi-User Licensing streamlines software access for organizations with multiple users, shifting from individual codes to group-based solutions.
Key Features:
Configurations for simple activation limits or concurrent usage.
Efficient management of entitlements across user groups.
Benefits:
Simplifies license management for vendors and customers.
Attractive pricing models for organizations.
Trends:
Cloud-based dynamic scaling and cross-device usage.
AI-driven optimization for user allocations.
Support for educational and remote work environments.
Multi-User Licensing is best for vendors serving business customers or large deployments.
Consumption-Based Licensing tracks and charges for actual software usage using units called consumption tokens, enabling flexible and fair pricing.
Key Features:
Allocates tokens to license codes or users for purchasing software or features.
Supports usage-tracked contracts and pay-as-you-go models.
Benefits:
Aligns costs with value derived.
Opens up new markets by making software accessible to light users.
Trends:
Popular in SaaS and cloud services.
AI/ML for usage predictions and dynamic pricing.
Granular tracking, down to API calls or processing time.
Consumption-Based Licensing is ideal for organizations optimizing costs based on usage or offering flexible pricing to customers.
Maintenance Contract Licensing manages ongoing support and update services alongside software licenses, giving a comprehensive view of customer entitlements and generating additional revenue streams.
Key Features:
Associate maintenance contract expiration dates with licenses or user accounts.
Enables seamless tracking of support and update eligibility.
Benefits:
Enhances customer relationships and ensures recurring revenue.
Aligns support services with licensing management.
Trends:
AI-driven personalized maintenance offerings.
Tiered maintenance contracts for varying support levels.
Automated support and self-healing software.
Maintenance Contract Licensing is valuable for vendors that provide regular updates or ongoing support. It ensures customer engagement and stable revenue.
Concurrent or floating licensing offers a flexible approach to managing multi-user software access. Rather than tying licenses to individual users or devices, a pool of licenses is shared among a larger group. When users launch the software, they draw from this pool; when finished, the license returns to the pool for others to use.
Key Features:
Maximizes software utilization and minimizes costs, especially for organizations with varying usage patterns or shift-based workflows.
Suitable for businesses with fluctuating software needs.
Offers cost efficiency and flexibility, allowing organizations to optimize software investments.
Vendor Benefits:
Enables attractive pricing models for business customers.
Ensures fair compensation for software products.
Considerations:
Requires careful monitoring to avoid overuse.
Users may face access issues during peak times if all licenses are in use.
Trends:
Growing adoption of cloud-based concurrent licensing.
Integration with AI/ML for predictive analytics and usage optimization.
Hybrid models combine concurrent and subscription-based licensing.
Concurrent licensing is ideal for organizations with a large pool of potential users but only a fraction needing access at any given time, maximizing value and efficiency.
End Date-Based Licensing ties software access to a specific expiration date, after which the software ceases to function unless renewed.
Key Features:
Licenses are valid only up to a predetermined future date.
Enforces contract durations and time-limited access.
Benefits:
Aligns software access with contract terms.
Simplifies compliance and renewal management.
Trends:
Integration with automated billing and renewals.
Dynamic end dates based on usage or conditions.
AI for optimal license durations and personalized renewals.
End Date-Based Licensing is suited for subscription services and organizations needing strict usage periods.
We've worked with many software vendors over the years. In each engagement, we've identified several key stakeholders who must be involved in the project.
Typically, we start working with product management—the people responsible for an entire portfolio of applications. They take products to market, determine packaging and pricing, and develop strategies to sell capabilities to the user base. Product management is usually our first point of contact.
Engineering works closely with product management. As a full entitlement management platform, Zentitle provides powerful technology that integrates with your tech stack, abstracting go-to-market aspects from your underlying applications. This gives engineering the leverage to focus on building core functionality without getting mired in product marketing details. Engineering is key for implementing features that respond to the entitlement management system.
IT and Operations teams are essential back-office contributors who coordinate everything. Sales Operations, in particular, streamlines the quote-to-cash process, ensuring orders are fulfilled with the appropriate entitlements that customers can activate.
Finance and Legal also have significant interests in this space, as it forms the foundation for revenue recognition. Legal ensures compliance, and sometimes there's a dedicated compliance function to verify that customers adhere to license terms. The entitlement management system helps document, audit, and demonstrate this compliance.
From a customer-facing perspective, Support and Success teams rely heavily on the entitlement view of customer accounts. When addressing customer issues, they can access vital information, including user rights, usage history, and application access patterns, to provide the best possible support.
While these are our primary stakeholders, we often work with other areas like project management. We look forward to partnering with your team to make your entitlement management and software monetization project successful.
SaaS-based entitlement management, on-premises licensing, hardware-based licensing, or a hybrid is possible with Zentitle2.
Two licensing model types are widely used in software: SaaS (Software as a Service) and On-Premise. These two models represent fundamentally different approaches to accessing, using, and managing software, and each has its unique set of considerations concerning licensing and monetization.
The SaaS model is a modern approach to software delivery. Under this model, users use the software via the Internet, often on a subscription or usage basis. The software is hosted on the provider's servers, and users can access it using a web browser. The key advantage of this model is that it eliminates the need for organizations to install and run applications on their systems.
On the other hand, the on-premises licensing model is more traditional. A perpetual or subscription model often requires the purchase of a license for each piece of software. The software is then installed on the company's servers and each user's system in the case of a B2C desktop application. Once installed, it can be offered as part of a floating pool of licenses where the applications are shared or on an individual-use basis. Installing on both servers and desktops means deploying the licensing code embedded into the application, which alone requires more time, testing, and consideration of security issues.
In conclusion, both the SaaS and On-Premise models have their advantages and trade-offs, and from a software licensing standpoint, a different approach from engineering and product teams.
The SaaS application deployment model differs from on-premise as the security requirements differ significantly. SaaS deployments tend to be driven by connectivity to various systems and often to identity as the means of authentication and connection with the end user. They mostly consume API calls and don't require as much testing or engineering to roll out.
SaaS deployments still get all the benefits of Zentitle2 in creating an “abstraction layer” that frees the engineering, product, and other teams to be more agile, price, and package easily and go to market faster. These deployments may be easier, but they can also go to market in sophisticated ways with business models that allow a mix of subscription, usage, and other modern models easily and quickly.
On-premise deployments tend to be far more varied and complex, often requiring deployment into dark (offline) sites, with pools of concurrent network seats and millions of user desktops in the B2C model. In each case, there's more security, often the need for SDKs and specific OS targeting, and issues relating to virtual machine cloning and piracy.
In addition, entitlement management tends to have more moving parts, often including license codes (activation codes) distributed via channels, a store.
Or the need to enable a network-based license server in a corporate network that needs activating and deploying to control volume licenses.
In these cases, Zentitle2 enables fast and simple deployment, as we provide the connectivity between your application and our licensing cloud. As with SaaS, we not only provide APIs but also all the other infrastructure, security, and client-based SDKs needed to roll out effectively.
With Zentitle2 you can authenticate end users to entitlements with either a license code (activation code) or their username (Account-based licensing/identity licensing) and then choose the type of deployment, be it SaaS, on-premise, or hybrid (plus hardware/iOT), that meets your needs.
In summary, Zentitle2 allows you to authenticate users in any way you wish, to deploy via s SaaS or on-premise use case, and to offer a B2C desktop, seat, or a large network of users on an intranet. You can sell via seats, usage, subscriptions, perpetual, or a blend of any pricing model you wish. You can connect Zentitle to other systems like CRM, ERP, billing, and e-commerce to automate the whole lifecycle.
Zentitle2 is:
A “single source of truth”.
One platform for any product, model, customer, business case, and go-to-market strategy.
One repository for all your product entitlement data and insights.
The entitlement database of record.
Zentitle2 removes the business state, pricing & packaging logic that doesn’t belong in the application and enables your team to go to market fast no matter the deployment model.
Network Licensing manages software access and entitlements within local area networks (LANs), especially in environments with limited or no internet connectivity. Vendors deploy a local licensing server within a customer’s network to manage software entitlements across multiple computers, devices, or users.
Key Features:
Enforces licensing restrictions and tracks usage even in offline or restricted network environments.
Supports organizations with high-security requirements or complex network infrastructures.
Benefits:
Flexibility in deployment options.
Maintains control over software distribution and usage in challenging network conditions.
Trends:
Integration with edge computing and blockchain for secure, decentralized licensing.
Evolving to manage IoT ecosystems and virtualized networks.
Considerations:
Requires dedicated hardware or resources for the on-premises licensing server.
Best suited for industries with strict data privacy regulations or unreliable internet access.
Network Licensing is essential for organizations needing reliable software access control in restricted or offline environments.
Suite-based licensing simplifies software distribution and access management by shipping a single package containing all versions or components of a software suite. Access to specific features or applications is controlled through licensing, not separate installations.
Key Features:
Supports multiple tiers (e.g., Lite, Standard, Pro) or distinct applications within one package.
Customizes access to features based on user entitlements.
Vendor Benefits:
Streamlines product management and upgrades.
Reduces engineering complexity by avoiding multiple separate versions.
Trends:
Integration with AI for personalized suite configurations.
Microservices architecture for granular control.
Cloud-based feature delivery and IoT expansion.
Suite-based licensing is ideal for vendors offering multiple product tiers or comprehensive suites, enabling instant upgrades and tailored solutions.
You can lower SKU variants, instead using licensing to decide what version the customer gets, all on the same common hardware.
The full device lifecycle is taken care of from Manufacturing Provisioning through to End-User consumption, which can be in any environment, online or offline.
Up-sell opportunities, which can be instantly delivered via the licensing mechanism, allow you to further monetize the hardware that your customers already own.
Zentitle can control access to the services your hardware is connected to.
If you specialize in Intelligent Devices or sub-components, whether in consumer, professional, or industrial markets, you can leverage the Zentitle Licensing and Analytics platform to control, measure, and monetize your offerings.
Whether you produce or sell metal servers, cloud servers, VM Servers, or Software for use on those servers, Zentitle Cloud-Based Licensing & Analytics puts you in control. Secure your revenue with secure, controllable customer entitlements.
Companies that produce machinery and electronics for industrial use can ensure that their customers are using their hardware as sold by changing customer entitlements in the field via Cloud-Based Licensing.
Whether the hardware you sell is Consumer Products or specialist hardware used by professionals, you can now benefit from proven Licensing and Analytics. Deliver your solutions more flexibly without sacrificing control.
The world of Consumer Electronics hardware, driven by IoT, is becoming empowered by Licensing and Analytics. You can gain invaluable insight and control while delivering more value to your customers.
Some vendors believe an identity-based approach is best, but we disagree. It's highly restrictive and rooted in the vendor's background, having built identity systems first and then layered on some licensing capabilities.
It's far better to have a flexible entitlement and licensing-based system designed to support any form of deployment rather than to fix on a user-name-based approach—why compromise?
Sometimes, companies ask us about the difference between identity and entitlement management. While they have similarities in terms of providing access, they're fundamentally different systems. With an identity system, you're restricted to an identity-based approach (email address, username, password, etc.), which creates a one-size-fits-all model. This might work fine if you only need to manage identities with a lightweight set of attributes.
However, if you want to truly understand what rights you've sold at the company level and allow individuals, desktops, servers, devices, and other entities to access those entitlements, then entitlement management is what you need. Unlike identity-based systems that narrowly focus on authentication (who users are), entitlement management focuses on what rights users inherit from their association with an entity that has purchased various licenses.
Identity-based systems are particularly restrictive for desktop, server, or cloud-based deployments running in virtualized environments. Since you're only tying use to an identity, you can't distinguish between VMs or handle cloning effectively. Our entitlement platform, however, gives you direct management power over these scenarios.
Additionally, identity-based systems struggle with offline environments. If you have customers working in disconnected or air-gapped environments (what we call "dark sites"), leveraging a pure identity-based system becomes challenging. We integrate with IDPs, Okta, Auth0, etc., allowing you to support these flows within our standard entitlement management system, including offline use cases.
The channel presents another challenge. When working with channel partners who maintain an inventory of entitlements and licenses to sell, they can't effectively use a pure identity-based system because they don't yet know who'll buy the products. Entitlement management allows them to manage licenses without knowing the end users' identities.
Entitlement management provides flexibility even within a pure SaaS environment. It enables identity and license key/device-based activation, handles virtualization and offline scenarios, and offers superior channel partner support.
Zentitle by Nalpeiron delivers end-user entitlements across all ISV environments, from traditional Desktop and Server offerings to SaaS, Mobile, IoT, and hybrid solutions.
A common hybrid deployment scenario occurs when an ISV adds a SaaS component to their product offering.
For example, Desktop Software might include rights to access a SaaS platform where users can store and access materials. Adobe's Creative Cloud operates this way, providing access to a library of images that users can download for their graphics projects.
With Zentitle's Software Licensing, you can license software across any environment or combination of environments. This includes our Network Licensing, which supports customers operating Dark Sites where software cannot connect to the internet for licensing verification.
With Account-Based Licensing, which uses identifiers like usernames or email addresses for entitlements, users enjoy a modern, friction-free experience. Your customers can quickly start using your software while Zentitle manages and centralizes their entitlements across complex, disconnected systems.
You can mix and match any of our Licensing Models to suit your needs. For instance, you might use a perpetual license for Desktop software with a subscription model for SaaS components, or combine a Desktop subscription with consumption-based pricing for SaaS features.
Tools like Zengain and others monitor customer engagement and activity over time.
This helps the CS team monitor customers who might churn and ensure they have everything possible to prevent them from leaving.
Intelligent Churn Risk Monitoring
Continuous Engagement Monitoring: Track customer activity, feature adoption, and key product milestones throughout the customer lifecycle.
Early Churn Detection: Instantly identify drops in engagement, missed milestones, or declining usage patterns that signal potential churn risk.
Dynamic Engagement Scoring: Benchmark each customer’s activity against your Ideal User Profile, providing a real-time health score and highlighting accounts that need attention.
Switching from dongle-based licensing to Zentitle2's cloud-based platform offers a range of significant advantages for software vendors and their customers:
1. Elimination of Physical Dongle Hassles
No more tracking, shipping, or replacing physical dongles, which reduces logistical overhead and eliminates awkward customer moments.
Customers can access licenses instantly and remotely, improving their user experience and satisfaction.
2. Enhanced Security and Control
Zentitle2's cloud licensing provides real-time visibility into license usage. It allows you to monitor where licenses are active and shut down unauthorized use remotely, greatly improving intellectual property protection.
Dynamic entitlement management helps prevent unauthorized use and piracy, offering more robust security than physical dongles.
3. Greater Flexibility and Agility
Easily implement and modify licensing models (subscription, perpetual, usage-based, hybrid, etc.) without being tied to rigid hardware-based systems.
Licenses can be updated, extended, or revoked remotely, without requiring physical access to customer sites.
4. Automation and Integration
Licensing operations are automated and can be seamlessly integrated with order processing, CRM (like Salesforce), and e-commerce systems, reducing manual work and errors.
Customers can self-manage their licenses through intuitive portals, further reducing support burdens.
5. Improved Customer Experience
Customers benefit from easier compliance, smoother license management, and the ability to manage their own entitlements.
Support teams report fewer licensing-related issues, leading to higher satisfaction and lower support costs.
6. Scalability and Reliability
Zentitle2's platform is enterprise-ready, has proven uptime, and has the ability to handle billions of transactions monthly, making it suitable for companies of any size.
The solution supports online and offline licensing scenarios, ensuring flexibility for diverse deployment environments.
7. Fast Implementation and ROI
Many companies have reported rapid deployment and immediate operational improvements, with some able to implement Zentitle2 in just a day.
Moving away from dongles and legacy systems often results in substantial cost savings in licensing, service, and support.
"With Zentitle2, we can finally stop stressing over licensing issues and focus on what we do best: building great software." – David O'Neal, Product Line Director, New River Kinematics.
"Our support burden due to licensing has dropped away and things work smoothly." – Jonathan Pace, COO, Alibre.
"One of our major concerns was reducing piracy, and Zentitle2 has basically enabled us to significantly improve our security in that regard." – Steve Cooper, Director of Product Management, Smith Micro.
Physical logistics
Required
Eliminated
Security
Hardware-dependent
Real-time, remote, automated
Flexibility
Limited
High (multiple models)
Automation
Minimal
Extensive (APIs, integrations)
Customer self-service
No
Yes
Scalability
Hardware-limited
Enterprise-ready
Support burden
High
Reduced
Switching from dongle-based licensing to Zentitle2 delivers modern, secure, and flexible licensing operations that empower software companies to innovate, scale, and delight their customers.
Definition: Customer Success (CS) is a proactive, organization-wide discipline focused on helping customers achieve their desired outcomes while using your product or service. It aims to maximize customer value, drive product adoption, and foster long-term relationships, resulting in increased retention, expansion, and advocacy.
Key Concepts:
Proactive Engagement: CS teams anticipate customer needs and reach out before issues arise.
Value Realization: Ensures customers achieve the outcomes that led them to purchase.
Cross-Functional: Involves collaboration between sales, product, support, and other teams.
What CS is Not:
Not just customer support or account management.
Not reactive or solely focused on problem resolution.
Why It Matters: Effective Customer Success reduces churn, increases revenue, and turns customers into advocates.
Reducing customer churn requires a combination of proactive engagement, data-driven insights, and a relentless focus on customer value. The most effective strategies, supported by industry research and best practices, include:
1. Analyze Why Churn Occurs
Conduct exit interviews and analyze customer feedback to understand the root causes of churn.
Use this insight to address product gaps, service issues, or unmet expectations.
2. Engage with Your Customers
Maintain regular, proactive communication through check-ins, personalized messages, and value-driven touchpoints.
Proactive outreach helps identify and resolve issues before they lead to churn.
3. Educate and Onboard Customers Effectively
Implement a robust onboarding process with interactive tutorials, welcome emails, and onboarding calls to ensure customers realize value quickly.
Ongoing education through webinars, guides, and support resources increases product adoption and satisfaction.
4. Identify At-Risk Customers Early
Leverage predictive analytics and customer health scores to spot early warning signs of churn, such as reduced engagement or support requests.
Segment customers based on risk and prioritize high-value accounts for intervention.
5. Offer Incentives to Retain Customers
Provide targeted discounts, loyalty programs, or special offers to customers who show signs of leaving or are approaching contract renewal.
6. Collect and Act on Customer Feedback
Regularly survey customers to gauge satisfaction and gather actionable insights.
Use feedback loops to continuously improve products and services.
7. Personalize Customer Experiences
Tailor communications, offers, and support to individual customer needs and preferences.
Use customer data to deliver relevant, timely interactions that demonstrate value.
8. Provide Excellent Customer Service
Ensure support teams are empowered to resolve issues quickly and effectively.
Immediate and 24/7 support can be a major differentiator, especially for global or SaaS businesses.
9. Build a Customer Community
Foster loyalty and engagement by creating forums, user groups, or events where customers can connect and share experiences.
10. Address Involuntary Churn
Use account updater services and dunning emails to recover failed payments and prevent unintentional cancellations.
11. Focus on Your Most Valuable Customers
Dedicate customer success managers (CSMs) to high-value accounts to maximize their satisfaction and long-term retention.
12. Continuously Improve Your Product
Use customer insights and market trends to enhance your offering, ensuring it meets evolving customer needs and expectations.
By systematically applying these strategies—analyzing churn, engaging proactively, personalizing experiences, and focusing on value—you can significantly reduce customer churn and build a more loyal, profitable customer base.
Tools like can help your team easily manage the process.
Customer retention analytics collects, tracks, and analyzes customer data to understand why customers stay loyal to a business—or why they leave—so that companies can take targeted actions to reduce churn and increase long-term value. Unlike general analytics, which may focus on broad business metrics or product usage, customer retention analytics focuses on the factors that drive ongoing customer relationships and repeat business.
These analytics measure the relationship between a customer and a brand, helping organizations predict when and why a customer might churn. By examining metrics such as purchase history, repeat buying behavior, engagement frequency, support interactions, and reasons for cancellation, businesses can identify patterns that signal satisfaction or dissatisfaction. This data-driven approach enables companies to proactively address issues, improve customer experiences, and boost retention rates.
There are several types of customer retention analytics, each offering unique insights:
Periodic Retention Analytics: This method tracks user activity or engagement within specific cohorts over set periods (days, weeks, months) to observe how many customers remain active, providing a snapshot of customer "survival" over time.
Cohort Analysis: Groups customers by shared characteristics or behaviors (such as sign-up month) and tracks their retention rates to identify when and why drop-offs occur.
Funnel Analysis: Examines where users drop off in the customer journey, highlighting friction points or stages with high churn.
Predictive Analytics: Uses historical data and machine learning to forecast which customers are at risk of churning, allowing for proactive intervention.
Diagnostic Analytics: This type of analytics pinpoints the reasons behind churn by analyzing customer feedback, support tickets, and engagement data so businesses can address the root causes.
Prescriptive Analytics: Goes beyond prediction to recommend specific actions to improve retention, such as personalized offers or targeted engagement campaigns.
Key metrics tracked in customer retention analytics include churn rate, retention rate, customer lifetime value, repeat purchase rate, and engagement scores. By leveraging these insights, companies can identify high-value customers, optimize engagement strategies, and make data-backed decisions to improve loyalty and lifetime value.
Customer retention analytics provides a comprehensive, data-driven roadmap for understanding and improving customer loyalty. It empowers businesses to spot patterns, identify at-risk segments, and take strategic actions that reduce churn and drive sustainable growth.
Sales analytics tools are purpose-built to address the unique requirements of sales teams, distinguishing them from general analytics or product analytics platforms. Unlike product analytics, which centers on understanding how users interact with a product, tracking feature usage, and optimizing in-app experiences, sales analytics zero in on the sales process itself. This includes monitoring the performance of the sales funnel, analyzing conversion rates, and providing robust sales forecasting. The goal is to improve sales efficiency and effectiveness by delivering actionable insights directly supporting sales objectives.
Sales teams operate on fast-paced cycles and require data presented in a way that aligns with their daily routines and workflows. These tools are designed for ease of use, often featuring dashboards and reports tailored to track pipeline health, quota attainment, lead progression, and win/loss analysis. This focus on the sales workflow ensures that the analytics are immediately relevant and actionable for sales professionals, rather than being generalized metrics that might be more useful to product managers or marketers.
Furthermore, sales analytics tools are critical throughout the entire customer lifecycle. They enable sales teams to influence the initial sale and subsequent stages such as onboarding, adoption, and ongoing account management. By integrating with customer lifecycle management platforms, sales analytics tools can help identify upsell and cross-sell opportunities, monitor customer engagement post-sale, and flag accounts that may need additional attention to prevent churn. This holistic approach empowers sales teams to contribute to long-term customer success, not just short-term revenue.
In summary, sales analytics tools are specialized solutions tailored to sales teams' data needs and working patterns. They provide targeted insights that drive sales performance and support the broader customer journey, ensuring the sales function is closely aligned with revenue goals and customer success outcomes.
Improving Net Dollar Retention (NDR) requires a holistic approach that focuses on both reducing revenue loss (churn and downgrades) and expanding revenue from your existing customer base (upsells and cross-sells). Here are proven strategies, supported by industry best practices and expert sources:
1. Prioritize Customer Success and Retention
Invest in a dedicated customer success team to ensure customers achieve their desired outcomes and maximize value from your product.
Proactively engage customers through regular check-ins, personalized onboarding, and ongoing training to build strong relationships and address issues before they escalate.
Use customer health scores and CRM data to identify at-risk accounts early and intervene with targeted support or incentives.
2. Optimize Your Onboarding Process
A smooth, value-driven onboarding experience reduces early churn and sets the stage for long-term engagement.
Provide personalized support, clear product education, and accessible resources to help new customers realize value quickly.
3. Increase Product Adoption and Usage
Encourage deeper product adoption through customer education, in-app guidance, and accessible help centers.
Regularly update your product based on customer feedback, adding features and improving usability to keep customers engaged and invested.
4. Implement Effective Upselling and Cross-Selling
Use data analytics to identify customers ready for upgrades or complementary products.
Prompt users to upgrade by highlighting feature limitations or usage thresholds with contextual in-app messages.
Tailor upsell and cross-sell offers to specific customer segments based on their needs and usage patterns.
5. Strengthen Customer Engagement and Community
Foster a sense of community with webinars, forums, and events where customers can share best practices and feedback.
Regular engagement increases loyalty, reduces churn, and creates more opportunities for expansion.
6. Leverage Customer Feedback and Analytics
Collect and analyze feedback to understand customer needs, pain points, and reasons for churn.
Use this insight to refine your product, improve service offerings, and tailor engagement strategies.
7. Personalize Experiences and Segment Your Customer Base
Segment your customers by behavior, demographics, or business type to tailor communications, offers, and support.
Personalization increases the relevance of your outreach and the likelihood of expansion.
8. Monitor and Adjust Pricing Strategies
Regularly review your pricing tiers and feature allocations to ensure customers perceive value at every level.
Adjust pricing or features if you notice frequent downgrades or feedback about value gaps.
9. Set Clear Goals and Track KPIs
Establish NDR targets and supporting metrics (like upsell rate, churn rate, and product adoption).
Use dashboards and reporting tools to monitor progress and quickly identify areas for improvement.
Customer Success
Proactive outreach, onboarding, health scoring, ongoing support
Product Optimization
Regular updates, feature enhancements, user feedback loops
Upselling & Cross-selling
Contextual in-app prompts, data-driven targeting, personalized offers
Customer Engagement
Community building, webinars, forums, loyalty programs
Analytics & Segmentation
Usage tracking, customer segmentation, tailored engagement
Pricing & Value
Pricing reviews, value-based feature allocation
Goal Setting & Monitoring
NDR targets, KPI dashboards, trend analysis
By focusing on these strategies—delivering value, reducing churn, expanding within your customer base, and using data to guide decisions—you can significantly improve your Net Dollar Retention and drive sustainable, long-term growth.
Tools like can help your team with NDR.
Early churn—customers leaving within the first few months—is often rooted in a poor onboarding experience. A well-designed onboarding process is one of the most effective ways to reduce early churn, accelerate product adoption, and build lasting customer relationships. Here are the most effective strategies, backed by industry best practices:
1. Make Onboarding Clear, Simple, and Structured
Break onboarding into manageable steps using checklists and step-by-step guides, so users always know what to do next and don't feel overwhelmed.
Focus on delivering "quick wins" early, helping users experience value as soon as possible (e.g., setting up their profile or completing a key action).
2. Personalize the Experience
Segment users by role, goals, or experience level and tailor onboarding paths accordingly.
Use dynamic onboarding flows and in-app messages to guide users based on their actions and needs.
Personalization helps users feel supported and ensures the guidance they receive is relevant and actionable.
3. Centralize and Streamline Resources
Provide easy access to onboarding content such as video tutorials, FAQs, and product walkthroughs, so users can find help when needed.
Avoid information overload—introduce resources incrementally and contextually.
4. Communicate Transparently and Proactively
Set clear expectations about the onboarding journey, timelines, and milestones.
Maintain open lines of communication—let customers know what's happening, what's next, and who to contact for help.
Regularly check in with new users to answer questions and offer assistance.
5. Foster Early Engagement and Relationship Building
Use welcome emails, personalized greetings, and initial calls to make customers feel valued from day one.
Engage multiple stakeholders (not just the main contact) to build broader relationships and ensure organizational adoption.
6. Collect Feedback and Iterate
Incorporate opportunities for feedback during and after onboarding.
Use surveys or direct conversations to identify pain points and continuously improve the process.
7. Provide Ongoing Education and Support
Onboarding shouldn't end after setup. Offer ongoing training, webinars, and tips to help users deepen their product knowledge and engagement.
Make support easily accessible for new users with questions or obstacles.
8. Track and Optimize Onboarding Metrics
Monitor key metrics such as time to first value, completion rates, and early churn to identify bottlenecks and areas for improvement.
Regularly review and refine your onboarding process based on data and user feedback.
Companies that implement these strategies have reported:
40% decrease in early churn rates
30% increase in feature adoption
50% reduction in support tickets
Structured, step-by-step onboarding
Reduces overwhelm; increases completion and activation
Personalization
Boosts engagement and relevance for each user
Centralized resources
Empowers users to self-serve and solve issues quickly
Transparent communication
Builds trust and sets clear expectations
Early engagement
Fosters relationships and accelerates adoption
Feedback loops
Enables continuous improvement of onboarding
Ongoing education
Deepens product usage and long-term retention
Metrics tracking
Identifies and fixes onboarding bottlenecks
In summary:
A straightforward, personalized, supportive onboarding process is your most powerful tool for reducing early churn. By guiding users to value quickly, communicate proactively, and continuously improve based on feedback and data, you set the stage for long-term customer success.
Tools like can help your team easily manage the process.
Tools like Zengain and others score your customers' engagement using various metrics based on user activity.
This engagement over time helps predict if the customer will churn and provides an early warning system so the CS team can remediate.
Intelligent Churn Risk Monitoring
Continuous Engagement Monitoring: Track customer activity, feature adoption, and key product milestones throughout the entire customer lifecycle.
Early Churn Detection: Instantly identify drops in engagement, missed milestones, or declining usage patterns that signal potential churn risk.
Dynamic Engagement Scoring: Benchmark each customer’s activity against your Ideal User Profile, providing a real-time health score and highlighting accounts that need attention.
Definition: ACV is the average annualized revenue per customer contract, excluding one-time fees.
How It’s Used:
Measures the value of customer contracts for SaaS and subscription businesses.
Useful for sales forecasting and performance benchmarking.
Formula:
ACV = Total Contract Value / Number of Years
Example: A 3-year contract worth $60,000 has an ACV of $20,000.
Bookings: The total value of contracts signed in a period, regardless of invoicing or revenue recognition.
Billings: The amount invoiced to customers during a period.
Revenue: The amount recognized as earned according to accounting standards.
Why It Matters: Understanding the distinction helps with accurate forecasting and financial reporting.
Net Dollar Retention (NDR) is a critical metric for subscription-based and SaaS businesses that measures how much recurring revenue is retained from existing customers over a specific period, after accounting for revenue expansion (such as upsells and cross-sells), downgrades, and churn. Unlike basic retention metrics, NDR provides a comprehensive view of both the losses and gains within your existing customer base, offering a more nuanced understanding of customer value and business health.
How NDR Works
NDR tracks the changes in revenue from your current customers, excluding any revenue from new customers acquired during the period. It reflects the net effect of customers upgrading (expanding), downgrading (contracting), or leaving (churning). This makes NDR a powerful indicator of whether your company is successfully growing revenue from its installed base or losing ground due to customer attrition or reduced usage.
NDR Formula
The standard formula for calculating Net Dollar Retention is:
Starting MRR: Monthly recurring revenue at the beginning of the period
Expansion MRR: Additional revenue from existing customers (upsells, cross-sells)
Contraction MRR: Revenue lost due to downgrades by existing customers
Churned MRR: Revenue lost from customers who cancel or do not renew
Example Calculation
If a company starts the month with $100,000 in MRR, gains $20,000 from upsells, loses $10,000 from downgrades, and $5,000 from churn, the NDR is:
An NDR above 100% means your existing customers are, on average, spending more over time, even after accounting for losses. An NDR below 100% signals that revenue from existing customers is shrinking.
Why NDR Matters
Growth Indicator: A high NDR shows strong product-market fit, customer satisfaction, and successful expansion strategies. It's a key driver of sustainable, efficient growth.
Benchmarking: NDR allows for apples-to-apples comparisons across companies and periods, as it's expressed as a percentage and excludes new customer revenue.
Strategic Focus: Improving NDR often costs less than acquiring new customers, emphasizing the importance of customer success, upsell/cross-sell programs, and churn reduction.
Best Practices to Improve NDR
Invest in customer success to drive adoption and satisfaction
Identify and act on upsell and cross-sell opportunities
Proactively address customer issues to prevent downgrades and churn
In summary, Net Dollar Retention is a vital metric that reveals how effectively your business retains and expands revenue from its existing customers. It provides actionable insights for growth, customer engagement, and long-term business health.
Customer Lifecycle Management (CLM) in the context of B2B SaaS refers to the strategic process of managing and optimizing every stage of a customer's journey-from their first interaction with your brand, through onboarding, ongoing engagement, renewal, and ultimately, advocacy. This approach is essential for SaaS businesses, where recurring revenue, customer retention, and long-term relationships are key to sustainable growth.
High Acquisition Costs: B2B SaaS companies often face significant costs to acquire customers, making it critical to retain and maximize the value of each customer over time.Subscription-Based Revenue: The SaaS model depends on renewals and expansions, not just one-time sales, so ongoing engagement and satisfaction drive business success.Competitive Advantage: Effective CLM enables companies to differentiate through superior customer experience, leading to higher loyalty, lower churn, and increased referrals.
While models may vary, most frameworks break down the SaaS customer lifecycle into several interconnected stages:
Awareness/Reach
Prospects become aware of your solution.
Marketing, content, and outreach to educate market
Acquisition
Engaging and converting prospects into paying customers.
Sales alignment, value communication, onboarding prep
Onboarding
Guiding new customers through setup and initial product use.
Training, support, ensuring early value realization
Engagement/Activation
Deepening usage and adoption of the product.
Regular check-ins, usage analytics, tailored support
Retention
Maintaining satisfaction and preventing churn.
Proactive support, addressing issues, delivering ROI
Expansion
Growing the account through upsells, cross-sells, or increased usage.
Identifying growth opportunities, value demonstrations
Renewal
Securing contract renewals and extending the customer relationship.
Health checks, addressing concerns, renewal incentives
Loyalty/Advocacy
Turning satisfied customers into advocates who refer others.
Gathering testimonials, referral programs, case studies
Personalized Customer Experiences: By leveraging data and CRM tools, SaaS companies can tailor interactions and support to each customer's needs, increasing satisfaction and loyalty.Proactive Support: Customer Success Managers (CSMs) use analytics to identify at-risk accounts and intervene before issues escalate, reducing churn and improving renewal rates.Continuous Feedback Loops: Regularly collecting and acting on customer feedback enables iterative improvements to products and processes, keeping the offering aligned with evolving customer needs.Cross-Departmental Alignment: Effective CLM requires collaboration between marketing, sales, and customer success teams to ensure a seamless customer journey.
Understand Your Audience: Develop detailed buyer personas and ideal customer profiles (ICPs) to tailor strategies for each lifecycle stage.Leverage Automation and Analytics: Use CLM software and CRM platforms to automate communications, track engagement, and surface actionable insights.Monitor Key Metrics: Track metrics such as customer health scores, churn rates, Net Promoter Score (NPS), and Customer Lifetime Value (CLV) to measure and improve performance.Foster Internal Collaboration: Ensure smooth handoffs and communication between teams to provide a consistent customer experience throughout the lifecycle.
Customer Lifecycle Management is a foundational strategy for B2B SaaS companies aiming for sustainable growth. By managing each stage of the customer journey with a data-driven, customer-centric approach, SaaS businesses can maximize customer lifetime value, reduce churn, and build lasting relationships that fuel long-term success.Here are common examples of B2B customer lifecycle metrics, organized by lifecycle stage:
Conversion Rate: Percentage of website visitors or leads that become customers.Customer Acquisition Cost (CAC): Total cost to acquire a new customer.Time to First Value: Time from initial contact to when the customer first receives value from your product.
Feature Adoption Rate: Percentage of new customers using key features within a set period.Onboarding Completion Rate: Proportion of customers who complete onboarding steps.
Customer Retention Rate: Percentage of customers retained over a period.Churn Rate: Percentage of customers lost in a given timeframe.Customer Health Score: Composite metric based on usage, engagement, and satisfaction.
Net Revenue Retention (NRR): Revenue retained from existing customers, including upsells and cross-sells.Expansion Revenue: Additional revenue from existing customers through upgrades or new products.Account Growth Rate: Growth in revenue or product usage within existing accounts.
Reactivation Rate: Percentage of previously churned customers who return.Win-back Conversion Rate: Success rate of campaigns targeting former customers.
Net Promoter Score (NPS): Measures customer willingness to recommend your company.Referral Rate: Percentage of new customers acquired via referrals.These metrics help B2B organizations understand and optimize every stage of the customer lifecycle, from initial acquisition to retention, expansion, and win-back efforts.
Zengain empowers B2B SaaS companies to excel at every stage of the customer lifecycle (excluding the initial awareness phase) with a suite of targeted capabilities:
Acquisition: Zengain provides deep insights into trial and early product usage, helping sales teams qualify leads and tailor their approach based on user behavior. Teams can engage high-potential accounts and speed up conversion by understanding how prospects interact with the product.
Onboarding: Zengain delivers actionable analytics that help teams track new customer product usage. Teams can proactively provide support and ensure customer success by quickly identifying potential friction points.
Engagement: Zengain gives customer success teams real-time visibility into account health and product adoption. This enables early intervention when engagement drops, reducing churn risk and ensuring continuous value delivery.
Expansion: Zengain analyzes usage patterns to identify accounts ready for upsell or cross-sell opportunities. Sales teams receive pre-qualified expansion leads, making it easier to grow revenue by recommending relevant features or licenses.
Retention & Renewal: Zengain's comprehensive lifecycle analytics help teams identify at-risk accounts before issues lead to churn. These insights enable data-driven renewal conversations and demonstrate ongoing solution value.
Advocacy: Zengain tracks customer engagement to identify satisfied users who make ideal candidates for testimonials or referrals, transforming happy clients into brand advocates.
In summary, Zengain serves as a central intelligence platform for revenue teams, integrating actionable analytics and opportunity insights across all post-awareness stages.
Save money with automation.
Speed up the order-to-cash process by streamlining operations.
Eliminate wasted time, money, and roadblocks to innovation by decoupling engineering from business.
Reduce customer frustrations, high support costs, and manual effort.
Drive new revenues with actionable analytics.
Fix frustrations with the existing hard
Engineering gets the ability to release features without having to consider monetization
Product teams get control over how offerings are packaged, priced, and managed
Companies that utilize an entitlement management service unlock efficient growth by monetizing flexibly vs. the standard “hard-coded” entitlement model of most SaaS companies
From a growth perspective, homegrown systems create considerable delays in time to value for monetization initiatives
Homegrown systems are opaque, unable to leverage product utilization data and pricing & packaging agility to drive optimizations
Homegrown efforts divert essential resources away from innovation
Focus on your core competency
Empower the whole business to move faster with agility and automation
Reduce waste, costs, and contingencies
Drive new revenues from existing and new customers
Free your teams to innovate!
By choosing a purpose-built monetization system, product teams can execute on growth strategies at speed. Frustrations for product leaders caused by significant and constant dependencies upon engineering can be reduced or eliminated when it comes to selling their products with new license models, pricing and packaging software products in new ways with much shorter lead times.
- Empower product and sales teams without the need for engineering involvement. - Decouple business logic from the code, managed by the product team to enhance flexibility. - Easily test and try different pricing, packaging, and business models. - Quickly adapt to market conditions, enabling the launch of new pricing at any time. - Avoid sales team requests for usage data and the time spent generating reports. - Enable sales to directly use actionable data with Zengain. - Add or change business models, editions, or products in minutes, not weeks. - Gather useful analytics data from unique licensing sources, offering detailed insights beyond standard statistics. - Provide engagement tools that assist the sales team in closing deals. - Utilize detailed engagement and usage data for predictive analytics.
Using a purpose-built software licensing and monetization system, engineers and engineering departments can focus on product innovation without complex hard-coding demands from product and sales leaders wanting to sell your product in different and new ways.
The demands upon engineering departments of software vendors to meet the growth strategies are hugely significant. Resources and attention of engineers are continually needed, most often taking focus away from the development of the products the vendor sells. Why might you be experiencing this?
It is expensive and time-consuming to build a basic entitlement system
It’s hard to change, hard to test, and requires constant ongoing maintenance
Code is “brittle” with complexity and conditionality that is highly complicated
Often a silo and disconnected from crucial business systems like billing, ERP, and CRMs
Creates lag and dependencies with key depts like sales and product teams
It limits innovation and agility and is opaque to business users, limiting competitiveness
Engineering can't build anything but a basic system; this means a disjointed, manual, and inflexible system to manage the business
What benefits can engineers and engineering departments gain from utilizing a software licensing system that caters to their needs? - The engineering team can concentrate on their core products, as the responsibility for pricing and packaging changes shifts away from them. - Business logic is separated from code and managed by business users, providing added flexibility. - It eliminates ongoing costs and risks associated with non-core capabilities. - It does away with the expenses of maintaining specialized infrastructure. - The system reduces risks linked to specialized personnel. - Provisioning and modifications are automated and seamlessly coordinated across product, CRM, and billing systems. - Establishes a single source of truth through a centralized customer state that enforces entitlements and monitors utilization.
With a purpose-built software monetization system, sales and customer success teams can drive revenue growth much more effectively. With actionable insights and tools designed to do just that, sales teams can close more deals, shortening the sales cycle. Account expansion is made much easier by identifying pre-qualified upsell opportunities driven by real usage data. Customer Success teams are also assisted in preventing churn with actionable insights.
Certainly, here's the revised text with bullet points for clarity: - Provide usage data to the sales team, from the trial phase to end-of-life. - Offer engagement tools that can help the sales team close deals. - Automate the POC/trial processes, saving time and reducing manual effort. - Identify members of the buying committee, enabling targeted efforts to close more deals. - Help teams understand who is engaged or not, allowing them to communicate with the right people. - Enable an understanding of the motivations of trial customers to focus sales messaging. - Speed up the sales cycle, making it easier and faster to close deals. - Provide detailed usage and engagement analytics designed for the sales team. - Deliver actionable analytics within the team's own CRM system. - Offer easy-to-understand metrics to focus on the best accounts. - Give early warnings on accounts that might churn, providing an opportunity to save them.
Using a purpose-built software licensing and monetization system, finance departments and CFOs can accelerate payments through automated processes and manual intervention. Delayed and late payments for existing accounts of your software and saas products can be resolved much quicker when customer billing departments are slow or non-responsive.
- Finance staff can easily access entitlements directly through the Zentitle UI, eliminating the need to work within the software back-end or seek assistance from engineering. - Control of entitlements via the Zentitle UI motivates customers to pay on time by allowing the option to switch "off" entitlements in the field. - Zentitle2's Total Cost of Ownership (TCO) is significantly lower than that of a self-managed entitlement solution. - The CFO can conduct audits on "who has what" using a "single source of truth." - The finance team can add notes and effortlessly track "who did what and when." - Customers or specific entitlements can be "suspended" due to non-payment. - A grace period feature enables finance staff to offer key accounts some time to settle their payments. - Integration with finance systems can be fully automated using our APIs. - Zentitle2 helps reduce risks and improve compliance.
Connect your systems and eliminate the potential errors that come from relying on manual processes. A built-for-purpose licensing and monetization system allows the automation of workflows and actions associated with licensing operations and customer access to the products they buy.
In addition to automations and connectivity, we provide time-saving tools like our customizable online self-service support for your end-users. This saves you time and money, not having to build critical support infrastructure while offering user-friendly ways to work with your users.
Self-serve end-user portal
Helpdesk support for end-users is made easier
Certainly! Here's the text with added bullet points for clarity: - Eliminate manual processes by automating licensing operations, thereby freeing up resources. - Connect systems to eradicate waste and manual tasks, accelerating team productivity and focus. - Boost revenues by enabling customer support/service teams to engage with customers directly, avoiding delays caused by other departments or manual systems. - Enhance customer satisfaction through quick identification and resolution of issues using automation and engagement analytics. - Allow end users to self-manage and review their licenses/entitlements via their own portal. - Achieve significant time savings by automating tasks with our APIs. - Reduce human error and manual control issues related to entitlements. - Increase customer satisfaction with quick, self-service options and portals.